|
why would the National Security Agency
be interested in cashless payments in 1996?
|
much more from cryptome
|
Wallet Observers
All of the basic off-line cash schemes presented in 3.3 can cryptographically detect the identity of multiple spenders, but the only way to prevent off-line multiple spending is to use a tamper-resistant device such as a smart card. One drawback of this approach is that the user must put a great deal of trust in this device, since the user loses the ability to monitor information entering or leaving the card. It is conceivable that the tamper-resistant device could leak private information about the user without the user's knowledge.
Chaum and Pedersen [6] proposed the idea of embedding a tamper-resistant device into a user-controlled outer module in order to achieve the security benefits of a tamper-resistant device without requiring the user to trust the device. They call this combination an electronic wallet (see Figure 4). The outer module (such as a small hand-held computer or the user's PC) is accessible to the user. The inner module which cannot be read or modified is called the "observer." All information which enters or leaves the observer must pass through the outer module, allowing the user to monitor information that enters or leaves the card. However, the outer module cannot complete a transaction without the cooperation of the observer. This gives the observer the power to prevent the user from making transactions that it does not approve of, such as spending the same coin more than once.
HOW TO MAKE A MINT:
THE CRYPTOGRAPHY OF
ANONYMOUS ELECTRONIC CASH Laurie Law, Susan Sabett, Jerry Solinas
National Security Agency 1996
|
| a Global cashless society...
Promis (Process Management Integration System) facilitating paperless manufacturing and comprehensive traceability
According to Lodato, improved x ray lithography techniques were critical to the development of 'emoney,'
i.e. cash cards. He was writing in the mid nineties, when emoney was believed to be a hot new technology,
and it was thought that people would stop using paper money and instead use plastic for anything.
Emoney hasn?t happened yet, but who knows, it might. At any rate, Lodato believed the Octopus wanted
to control the emoney industry. First of all, because of profits reckoned to be in the hundreds of
billions. And secondly, because of the information flows involved. By tracking how people spent money,
the Octopus could increase its own understanding and power of the world economy. But to control emoney,
the Octopus needed to control the new x ray lithography technique. This put the Octopus at odds with
Hampshire Electronics and Bizzy Bee Equipment. - Update
Probably within a 20 year period, E-Money will come about or a unified one world currency. We will be using smart cards. At present the basic problem with these smart cards is that they can be duplicated.
In order to stop the duplication one must embed chips that cannot be duplicated. Hence it is imperative to have chips with design rules of the order of 0.1 microns and they must be mass produced in a cost effective manner. No technology exists today to produce these Dram, Asic, etc. chips in mass production.
The only way to do this is via an x-ray lithography process and a unique step and repeat tool. Such tools will cost over $15,000,000 per tool and would have an extremely high throughput with at least a 70% efficiency, and no one person, company or nation could buy one in an undetected fashion. There will be no more counterfeiting.
This is why this high cabal, need to control this chip making and the x-ray lithography process.
Several years ago the head of Sematech personally told me over the phone that there is to be only one stepper manufacturer in the world for x-ray aligners. I didn't understand it; and thought that it didn't make sense... but it does now.
These tools are the printing presses for E-MONEY, the plates are the masks, etc... and the boys must control them entirely...so gold etc will have a different place in the world as it has today.
There will be a global centralized bank with several information reserve banks controlling regions of the world. Chip Tatum hinted about "the Corporation" and this centralized Global banking system. He said the cabal has members living in Jupiter Island in Florida. We have found that Douglas Dillon has a summer house at Jupiter Island. (It is alleged that he has connections with the Dominica Non Secret Echelon Project--See lower notes.) If what Tatum wrote in his Pegasus file is correct, he connects the Bush family to the Corporation. Nevertheless, the "Corporation" that Tatums speaks about fits directly with Echelon, and the secret NON USA base in Dominica. Tatum states that our past President George Bush is pushing "this Idea" through his NWO agenda. He also shows a letter signed by George Bush authorizing some WET operations. - The Octopus and the Physicist by Vince Lodato
The Global Fascist State
It is believed that there exists an "elite cabal" at the apex of banking and industry, operating through government and the media, and controlling our political, social and personal lives to ever-increasing degrees. This elite group has been pursuing its ambitions for centuries and is operating to an agenda entirely not in our interest. It has ruthlessly manipulated the political landscape via the strategic destabilization and reorganization of nation states; and its ultimate objective is to take the incredibly diverse range of human cultures once existing on Earth and slowly mould them into a single, homogenized trading and consuming block under their centralized control.
The principal means by which it is believed this group is seeking to do this is via the expansion of their own developmental prototype for world culture - America; a set of cultural values that is systematically being expanded across the world, progressively eliminating a wealth of ancient peoples and beliefs, and leaving in their place a standardized, consumerist stereotype.
The ultimate goal of this proposed elite group is to bring about a single global marketplace, controlled by a world government, policed by a world army, financially regulated by a world bank via a single global currency, and populated by a microchipped population connected to a global computer, a computer that both monitors and updates our personal location and financial status, and regulates our emotional state via transmitted electrical signals - technology that already exists.
This ambition of thus rendering the Earth a "prison planet" - a self-contained, interactive social structure under total centralized control - is chiefly being pursued via activities in two areas - commerce and culture. In "commerce," the elite group have created the corporations, the vehicles for the planet's enslavement, and in "culture," the elite group have created both the drivers and passengers of those vehicles - us.
Blueprint for a Prison Planet by Nick Sandberg
backup
|
|
|
The Octopus companies were first discovered by Danny Casolero and it cost him his life..
They say he committed suicide.
The Octopus companies are IBM, ATT, LOR, LMT GmH (hughes) and LEH. Rather than repeat what was published
see from nov 1999 to the present under vince...you CANNOT USE THE SEARCH routine but you have to check
by just scrolling the board....
1....IBM is a prime contractor for Echelon and in particular Project Echelon...see IBM abuses and
cover ups by NSA officials...BBE and Hampshire Instruments --two small american companies...destroyed
by IBM with the help of NSA officials....Joan Lodato, my sister murdered ...and Moshe Lubin of Hampshire
(hung himself)
2.....ATT has secured contracts using Project Echelon over NEC via use of ECHELON in Indonesia...
3....LMT/LOR involved in the x-ray lithography project both companies gained in the destruction of
Hampshire Insruments...
4....Secret private Echelon base discovered by Danny Casolero on the Island of Dominica...not USA
sanctioned.....put up by the Octopus companies...NSA involvement TBD????? ...
NSA employee Standorf conveyed to Casolero the hard evidence...Standorf shot in the head...
body found at National Airport in DC...and Casolero slit wrist...(they say)...sucide.
source
|
|
The Pegasus file
"The so-called Pegasus group's organizational structure as provided by Chip Tatum, demands recounting in detail.
The various presidential orders, which led to the formation and operation of the covert activities in which
Tatium and others participated, are significant for they constitute a secret government within a government.
This is the power that hides behind to open face of democratic government. Some have called this power
base "the Octopus". Activities include high level narcotics trafficking, illegal transfers of ultra-high
tech weaponry, money laundering on a massive scale and an odd "hit" or alignment to keep wobbly-kneed
individuals on the straight and narrow."
"...the question remains: What did George Bush intend to do with his 'black' $3.8 billion?
What was the ultimate purpose of the operation? Perhaps some of the money was to be used to grease
palms and otherwise finance Bush's bid for the presidency following the completion of President
Reagan's second term. Maybe it was used to finance other lucrative projects. Perhaps it was used
to be used to inject finanical muscle into another, grander scheme, of which Tatum has recently
spoken, involving George Bush's "scope and mission" paper for a New World Order.
A copy of the "scoping" paper supplied to Tatum by George Bush outlines the formation of a Corporation
whose purpose is to "...provide a central network of information, analysts and strategists on an
international basis in pursuit of world order and economic stability". The scope of the Corporation
involves four features:
1)Centralization of informational services.
2)Analysis of data by region-specific analysts;
3)Provided recommendations based upon analysts' reports by international experts;
4)Provide international master plan for world growth and economic stability.
The Corporation is to be privately owned with a board of directors "consisting of Twelve members,
elected annually by the shareholders. In addition there are five departments: "Data Resources,
Political Management; Economic Management; Military Management; Environmental Management". -
more
|
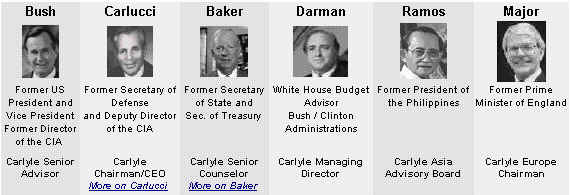
Is this corporation The Carlyle Group...?
|
The Octopus companies links to Carlyle
IBM
Consider Louis Gerstner, the CEO of IBM for seven or so years: During his tenure the following events occurred.
(1) IBM was criminally convicted of selling super computers to the Russians for atomic weapon research. IBM received only a $8.5M fine and it was in the news for only one day.
(2) IBM sold one the largest supercomputer in the world to China via Hong Kong. It is reported to be used in the Chinese Echelon project.
(3) IBM was caught in bribing and payoffs in a $250M contract with Banco Nacio in Argentina. The trail lead back to IBM Corporate in NY. IBM had a similar incidence in Mexico. IBM bought their way out of it via the political influence and money. Gerstner hired Podesta Associates. The owner of this firm has a brother who is chief of staff to President Clinton. Consequently, Gerstner has an in the White House.
(4) When Companies and individuals get in the way of their plan...they die!!!...Judge Bagnasco witness in Argentina. Other examples the murder of Joan LoDato in Kingston NY.
(5) Under Gerstner leadership IBM set up an Institute to tell governments how to act in the Information Age. Gerstner is a member of the Tri Lateral Commission, the CFR...and a voice in the Bilderbergers.
(6) Under Gerstner leadership, tens of thousands of Americans lost their jobs at IBM. These same jobs were and are being transferred to IBM China and IBM India.
(7) Gerstner has a modest salary of only a few million a year. However, over his tenure he made over one billion dollars from his stock options.... A poor boy who became rich...and sold his soul and lack of concern for the USA for money...This is an example of the new NWO leaders.
The Story of the Secret base on Dominica and the Murders that Followed.
Louis Gerstner Chairman of the Carlyle Group -
November 21, 2002 - The Carlyle Group announced that Louis V. Gerstner, Jr. will become chairman of The Carlyle Group effective January 7, 2003
Mr. Gerstner has been chairman of IBM since 1993, and served as chief executive officer of IBM from 1993 until March 2002. He retires as chairman of IBM at the end of 2002.
Mr. Gerstner was awarded the designation of honorary Knight of the British Empire by Queen Elizabeth II in June 2001.
Feb 2, 2006 - Also investing with the Carlyle Group is Novak Biddle Venture Partners, a Maryland-based venture capital firm. Command Information, headed by Tom Patterson, former chief strategist of e-commerce at IBM, also announced Thursday that Command Information has merged with Digital Focus, an IT services company. -source
ATT,
for much of the 20th century, AT&T was the world's largest firm, in terms of both revenue and market capitalization. It was the preferred safe "widows and orphans" stock. It was the home of Bell Labs, a spectacular source of innovation produced the transistor, the laser, and a number of Nobel Prize winners. It had amazing cash flow.
The article quotes, Clayton Christensen of Harvard Business School, author of the excellent book The Innovator's Dilemma as noting "The world is filled with companies that are marvelously innovative from a technical point of view, but completely unable to innovate on a business model." AT&T simply wasn't ready to compete after the 1984 breakup of its monopoly. It missed out on the rise of computers, on wireless technology, and on the Internet, even though it had years to adapt to those changes after the breakup. By the time AT&T started to adapt to what was changing, it was too late. - source
It was a long and bitter antitrust case. By court order, AT&T was divided up into seven regional Bell Operating Companies (RBOCs), along with a long-distance company (holding the AT&T name). The telephone research laboratory (Bellcore) was a resource shared by all.
The court decision was one of the biggest antitrust decisions ever. The most comparable forced breakup was that of Rockefeller's Standard Oil trust 1911. And as the Standard Oil dissolution led to regional "Baby Standards" (Sohio, Socal, Socony, etc.), so the Bell breakup led to "Baby Bells." source
Wei Deng is a Vice President focused on real estate opportunities in China. He is based in Beijing, China. Prior to joining Carlyle, Mr. Deng was a Vice President at Merrill Lynch in Beijing, where he focused on real estate investments in China. Prior to that, he was a Vice President at H&Q Asia Pacific focusing on private equity investments. He has also held numerous positions at both AT&T and MCI Worldcom in the U.S. - source
More on the Carlyle Groups connections
|
|
Concluding on the Octopus companies and repeating some of the above:
Consider LOR, it's on the NYSE. Check the company out. It is incorporated in Bermuda. Why is a $2 billion dollar American company that handles ultra secret projects incorporated in a foreign country? Back in the 1970, LOR had a big scandal and mob connections. Recently their is the problem of Bernie Schwartz, the CEO of LOR, and his contributions to the present Administration.
LMT when it was just Lockheed back in the 1970's had ties with the Yakuza. I know this is old information, but it shows these companies will and have dealt with anyone.
IBM corporation is a convicted felon as of last year [unkonwn yr]. Yes felon, for selling supercomputers to Russia. I assure you if you tried to do such a thing you would be in jail and they would throw away the key. But IBM just got a $8.5M fine and all was hush hush.
GmH and LOR just had a big investigation for selling missile technology to the chinese.
So in conclusion I would not worry about the NSA per se, but I am very concerned of the misuse of Project Echelon by these octopus companies. This could only occur if there are some bad apples in NSA. This may be a hard pill for some to take, but years ago when I consulted for the GAO on certain projects I use to say, "I found out that motherhood was prostitution."Dominica is real. The private Project Echelon is real. These companies are real IBM, LOR, LMT and GmH.
- source
|
LOR, = Loral space systems, Loral Bermuda, Loral Asia
|
Loral Space Systems - From Year of the Rat - How Bill Clinton Compromised U.S. Security for Chinese Cash,
by Edward Timperlake and William C. Triplett II:
In the early morning hours of February 15, 1996, a Chinese Long March 3B space launch rose a short distance off the launch pad and then fell over onto a local village with an incredible explosion. According to an Israeli engineer who witnessed the disaster, "thousands of corpses were loaded in dozens of trucks and buried in mass graves."...
Loral Space Systems, the builder of the February 15 satellite, had a problem. So did the Chinese launchers, who had such a poor reputation for reliability that they were uninsurable. Without insurance, Loral and the other U.S. firms could not use Chinese rockets to launch their satellites. Something had to be done to make the Chinese rockets more reliable if the satellite makers were going to save a dollar or two on launch fees. . . .
On April 14, 1998, the New York Times ran a major story by investigative reporter, Jeff Gerth -- "Grand Jury Probes Two Firms' Ties to China Missile Program" -- that linked Loral and its partner, Hughes Electronics, to China....
Under pressure from Congress, the National Security Council was forced to release a series of documents it would have preferred to keep secret. The substance of the allegations is as follows:
>> Without obtaining a proper license from the State Department, engineers for Loral and Hughes helped the Chinese make their rockets reliable. Not only did the engineers solve the immediate cause of the February 15 accident, they also recommended improvements to other areas of weakness in the Long March.
>> In May 1966, after the federal government found out about this, the U.S. Air Force did a classified study of the event and concluded that "United States national security has been harmed."
>> After a number of delays, the Justice Department began a federal grand jury investigation.
>> In February 1998 the Justice Department was closing in on Loral and Hughes when President Clinton approved a waiver allowing the free transfer to China of the same technology that Loral and Hughes were accused of transferring under the table. This severely undercut Justice's case.
National Security Council documents show that, although at the time of the February waiver National Security Adviser Sandy Berger knew Loral's conduct was "criminal, likely to be indicted, knowing and unlawful," he did not recommend against what amounted to a get-out-of-jail-free card for Loral.
>> Adding to the overall concern, the encoded portion of the Loral satellite was missing when the Chinese returned the debris from the February 1996 explosion. NBC has shown pictures of PLA soldiers picking through the crash site while U.S. officials were kept away for five hours.
Finally, after the Loral-Hughes fixes, the Chinese launch program now has a perfect record for reliability.
Then there is the question of the money. Loral Chairman Bernard Schwartz claims that it is only a "coincidence" that he, his family, and his employees were large donors to the Clinton-Gore cause and subsequently received favorable treatment from the administration ...
After Clinton and Gore were elected, they had something Schwartz wanted. In the summer of 1994 he wrote a check to the Democrats for $100,000.
Two months later he was on Ron Brown's trade delegation to China. Brown arranged meetings between Schwartz and Chinese officials.
In the 1993-1994 cycle, Schwartz contributed a total of $112,000 to the Democrats....
Everyone got what he wanted.
Bernie wrote a lot of checks. His personal contributions rose to an amazing $586,000 in the Clinton-Gore reelection cycle of 1995-1996. As of May 1998 Schwartz had contributed $421,000 to the Democrats' 1997-1998 campaign cycle. That makes him the number one contributor to the Democrats in both the 1995-1996 and 1997-1998 campaign cycles. Between 1992 and 1998 he has given the Democratic Party $1,131,000. His family, his companies, and his executives have given another $881,565 to Democratic candidates. Finally, he has contributed $217,000 to the Democratic Leadership Conference, a Clinton-associated think tank.
Grand total: More than $2.2 million to the Clinton-Gore ticket.
Bernie got his antitrust exemption for Loral.
On March 12, 1996, Clinton overturned an October 1995 decision by Secretary of State Warren Christopher and transferred authority for satellite export licenses to the Commerce Department.
Tiananmen waivers became routine for Clinton....
America's first line of defense against missile proliferation was dismantled. Loral would have gotten off the hook with the February 1998 Clinton waiver if somebody hadn't tipped off Jeff Gerth of the New York Times....
Equally important, Clinton and Gore were reelected....
From: Betrayal -- How the Clinton Administration Undermined American Security: . . .
President Clinton has turned upside down President Dwight D. Eisenhower's warning about a too-powerful military-industrial complex. Using the end of the Cold War as cover, and to please corporate bigshots targeted for campaign contributions, Clinton has loosened export controls on several high-technology sectors, including U.S. high-speed computer manufacturers, software makers, and communications satellite makers who want to sell to China. . . .
Two such companies are Loral Space & Communications, Ltd. and Hughes Electronics, both the subject of a federal investigation to determine how they passed embargoed militarily-useful rocket technology to Beijing without licenses.
At the time of the weapons technology transfers, Loral was headed by Bernard Schwartz, who has given hundreds of thousands of dollars to Clinton and the Democratic Party....
Shortly after the "decontrols" took place, American supercomputers began showing up in both Chinese and Russian nuclear weapons development centers -- helping to build nuclear arms that might one day be turned against the United States...* * *
|
From The Buying of the President 2000,
by Charles Lewis and The Center for Public Integrity:
It's one thing to macromanage the national political party from the White House in unprecedented fashion, and unabashedly sell access to the White House, Air Force One, Camp David, and so forth, to the party's biggest patrons....
But what if a President's naked malleability, his willingness to bend policies to money, actually violates and jeopardizes our national security? What if a U.S. company headed by the Democratic Party's most generous individual patron in the 1990s violates federal laws involving national security? And after this happens, what if the company continues to get government contracts and even an export waiver signed by the President himself, worth millions of dollars-- over the objections of the Justice Department prosecutors?
All of this did in fact occur, against a backdrop of espionage and intrigue, of dozens of illegal campaign contributions from foreign nationals with no real assets, of nuclear secrets systematically stolen from our most advanced laboratories over many years, and all of it led back to one country - China....
In 1992, after President Bush had approved a waiver, and an American satellite was subsequently launched on a Chinese rocket, several senators, including Al Gore, wrote to the Bush Administration to complain that China was using the launchings to "gain foreign aerospace technology that would be otherwise unavailable to it." ...
Unfortunately, far more than Chinese leaders were coddled by the Clinton-Gore Administration and the Democratic Party, under vastly more serious circumstances. . . . In its first four years, the Clinton Administration awarded ten waivers to China, one more than Bush. But the number of waivers in not really the issue.
Almost as soon as Clinton and Gore took office in January 1993, the Chinese and U.S. corporations doing business in China began lobbying intensely to "educate" the new administration to look beyond the country's poor human-rights record. In the 1992 election, dozens of U.S. companies active in China had given millions of dollars to the Democratic Party.
By May 1993 the President reversed his campaign posture and awarded China most-favored-nation trade status....
One of the most aggressive of those companies was Loral Space and Communications Ltd., which manufactures satellites and is headed by Bernard Schwartz. Loral and Schwartz have contributed at least $1.9 million to the Democratic Party since 1991...
In 1994, Schwartz was awarded one of the coveted seats on the late Commerce Secretary Ronald Brown's trade mission to China. Brown helped Loral seal a multimillion-dollar mobile telephone satellite network deal in Beijing....
During the 1990s the Chinese government courted companies like Loral to launch its satellites. Both Chinese and American companies wanted the U.S. government to loosen its export licensing rules regarding satellites. Specifically, they wanted satellite export licensing decisions to be made by the Commerce Department, not the more restrictive State Department.
Billions of dollars were at stake -- an estimated 14 commercial communications satellite launchings annually, each costing several hundred million dollars.
C. Michael Armstrong, then the CEO of Hughes Electronics Corporation ... met with then-Secretary of State Warren Christopher, and requested that satellites be regarded as commercial, as opposed to military, goods. Christopher agreed to conduct a detailed interagency review with officials from the Defense Department, the National Security Agency, the CIA, and other agencies.
Soon, however, a majority of the interagency group, including Christopher, had concerns about the security ramifications; disagreeing with Loral, Hughes, and the aerospace industry generally. They thus recommended that satellites continue to be categorized as military on the State Department's munitions list.
Commerce Secretary Brown, a former chairman of the Democratic National Committee and a prolific fund-raiser, appealed the decision to the President. Clinton sided with Loral and the industry, in a decision that was publicly announced in March 1996.
The Commerce Department thus was entrusted with the national security issues surrounding satellite technology.
Worse, weeks earlier a Chinese rocket carrying a $200 million Loral satellite had crashed seconds after liftoff in southern China, killing and injuring civilians on the ground. The China Great Wall Industry Corporation-- the Chinese government's missile, rocket, and launch provider-- asked Loral to help pinpoint the cause of the accident.
In the collaboration that ensued, engineers from Loral and other companies identified potential causes that the Chinese engineers had overlooked. As a result, China may be able to improve the accuracy of its intercontinental ballistic missiles (ICBMs), 12 of which are aimed at U.S. cities (including Honolulu and Pearl Harbor?)
The Pentagon and the CIA found that both Loral and Hughes had "greatly damaged U.S. national security." The State Department warned White House aides that Loral had engaged in "unlawful" and "criminal" activity. . . . The Justice Department began a formal criminal investigation into the matter.
Amid all this, in the chutzpah department, Loral had another satellite deal pending with the Chinese, and once again wanted a waiver from the President. "Sandy" Berger, Clinton's national security adviser, and other administration officials recommended that Loral be given the green light, although they acknowledged in a memo to Clinton that such a decision might be perceived as letting Loral "off the hook on criminal charges for its unauthorized assistance to China's ballistic missile program." Meanwhile, Justice Department prosecutors warned that approving the waiver request would seriously jeopardize the Loral investigation.
On Feb 18, 1998, the President approved the deal and signed the waiver....
The wheeling and dealing were not occurring in a vacuum. Months earlier, in July 1997, the President had been briefed that China, through years of spying and outright theft, had obtained some of the most sensitive U.S. military technology, including nuclear weapons design.
And the Democratic Party was deeply embroiled in scandal over illegal contributions from China, part of a systematic campaign to influence the 1996 U.S. presidential election. The Senate Governmental Affairs Committee had recently found "strong circumstantial evidence that the Government of the People's Republic of China was involved in funding, directing, or encouraging some of these foreign contributions."
Clinton had been criticized for months for repeatedly stonewalling requests from the Senate committee and the news media for information, and more than 45 witnesses had fled the country or invoked the Fifth Amendment. The President and his administration, the Senate committee found, "took no action whatsoever to persuade such individuals to cooperate."
More foreboding, 80 percent of the illegal foreign contributions had been raised by two longtime Clinton friends, John Huang and Charlie Trie. Huang took the Fifth and Trie fled to China. (Huang later decided to cooperate with the Justice Dept and pleaded guilty to one felony charge. Trie voluntarily surrendered to U.S. authorities in Feb 1998 and pleaded guilty to violating federal campaign finance laws the following May.)
At the very least, it strains credulity that any President, including Clinton, would have approved the multimillion-dollar waivers to this company under all these troubling circumstances in no money had passed into the party coffers. In fact, well over $1 million was lavished upon the Democratic Party....
In 1999, a select House committee chaired by Representative Christopher Cox, a Republican from California, produced an 872-page report that was unanimously approved by its five Republican and four Democratic members...
The committee found that China's "acquisition efforts [of American military technology] over the past two decades" had been a "serious, sustained" activity.
The committee specifically criticized Loral and Hughes for passing "illegally transmitted" information to the Chinese that was "useful for the design and improved reliability" of future Chinese ballistic missiles.
The report said that the Clinton Administration's policy of permitting businesses to police their own technology sales abroad has not worked, because the national security interest "simply may not be related to improving a corporation's 'bottom line.'"
But it sure worked well for the companies, China, and the Democratic Party....
|
# # #
NOW, IF ALL THIS IS NOT ENOUGH TO RUFFLE YOUR FEATHERS -- DID YOU KNOW THAT FRANCE'S
AXA FINANCIAL COMPANY IS THE #1 INSTITUTIONAL INVESTOR IN LORAL SPACE AND COMMUNICATIONS ?
AND THAT, AFTER MORE THAT A HALF-CENTURY, INVESTIGATIONS HAVE REVEALED THAT AXA FINANCIAL
MAY HAVE OBTAINED MUCH OF ITS WEALTH AT THE EXPENSE OF NAZI HOLOCAUST VICTIMS!
AND, FINALLY, DID YOU KNOW THAT AXA FINANCIAL IS ALSO THE #1 INVESTOR IN
GOLDMAN SACHS !
- source
|
|
Loral chief upbeat on China satellite export
Source: Reuters via Yahoo Published: 03/29/01 Author: Jim Wolf WASHINGTON, via Freepers
Chairman Bernard Schwartz said Thursday he was increasingly confident that the State Department would approve his company's long-delayed sale of a communications satellite to China.
``I'm more optimistic now than I was before,'' he told a news conference at a satellite industry conference. ``The new administration relieves the focus on the political issues to some degree.''
Bush administration officials have held ``constructive'' talks with Loral, manufacturer of the so-called ChinaSat8, on the ``merits'' of the deal, he said.
``And from that point of view, it's a more favorable climate,'' said Schwartz. The State Department had no immediate comment on the status of the export license request.
The license appears to have been ``caught up'' in a criminal investigation of whether Loral improperly gave China classified rocket expertise in 1996 after the failed launch of a Loral satellite, Schwartz said.
``I don't believe we did anything wrong'' in that case but there has been activity in the investigation, including occasional interviews of Loral employees, he said.
He said he did not expect any new evidence that could harm the company's reputation and would welcome a chance to confront any charges. The alleged violation of export control laws is an issue that has left Loral, a New York-based satellite and satellite-services provider, operating ``under that cloud,'' he said.
China Telecommunications Broadcast Satellite Corp. bought the satellite, valued at nearly $200 million, in 1998 with plans to launch it on a Chinese Long March rocket. But before the launch could take place, a Republican-led House of Representatives panel concluded that China had used launches of U.S.-built satellites to steal data that could be used to fine-tune Red Army missile-firing capabilities.
In the most recent action, the State Department's Office of Defense Trade Controls stopped short of rejecting Loral's application. Instead, it returned it without action on Jan. 4, two weeks before Bill Clinton left the White House, Loral said in a federal filing.
Loral made the disclosure because it might have to refund as much as $134 million in advanced funds from China. The company could also face $11 million in penalties if the sale did not go through.
Schwartz said the Chinese buyer ``continues to be very patient. They want the satellite,'' which would be used for television and data transmission and which is in storage in a Loral facility in Palo Alto, California.
According to the government, the sale was held up in 1998 to make sure it squared with the Arms Control Export Act, which seeks to curb the spread of ``dual-use'' goods that may have important military applications.
Schwartz said tighter export controls triggered by fears of Chinese espionage were crippling the U.S. satellite industry and undermining U.S. technological supremacy at a time of fierce global competition.
``I do believe that American industry has been damaged,'' he said, noting that the U.S. share of commercial satellite orders worldwide had fallen below 50 percent last year for the first time.
In the two years since Congress tightened export curbs on commercial satellites, the U.S. share of the global market has plunged to 45 percent from an average of 75 percent during the previous 10 years, the Satellite Industry Association, a trade group, reported last month.
Loral's top two U.S. competitors -- Hughes Electronics Corp.'s (NYSE:GMH - news) satellite manufacturing unit, now owned by Boeing Co. (NYSE:BA - news), and Lockheed Martin Corp. (NYSE:LMT - news) -- have also been charged with violations of export control rules, charges they have denied.
``It's criminal in my judgment,'' Schwartz said, referring to the export tangle and its impact on the U.S. satellite business. ``Something has to be done to repair the process.''
|
|
HUGHES, BOEING TO PAY MILLIONS
IN FINES FOR SELLING DATA TO CHINA
Penalty stems from exchange of rocket, satellite technology
March 6, 2003 - By Jeff Gerth, The New York Times WASHINGTON -sourced here
Two top American aerospace companies have agreed to pay a record $32 million in fines to settle civil charges that they unlawfully transferred rocket and satellite data to China in the 1990s.
The agreement, completed on Tuesday and released yesterday, comes two months after the State Department accused the companies, Hughes Electronics Corp., a unit of General Motors, and Boeing Satellite Systems of 123 violations of export laws in connection with the Chinese data transfers.
In a joint statement the companies said they "express regret for not having obtained licenses that should have been obtained" in the 1990s by a Hughes unit, the Hughes Space and Communications Co., which was acquired in 2000 by Boeing.
The companies also said that they "acknowledge the nature and seriousness of the offenses charged by the Department of State, including the harm such offenses could cause to the security and foreign policy interests of the United States."
The technology used to launch civilian rockets and satellites is similar to that used to launch missiles so there are tight burbs - mostly administered by the State Department - on the export of satellites, aerospace equipment and related defense services.
The Chinese have always insisted that their rocket and missile programs did not need help from American companies. But a string of Chinese rocket failures in the 1990s ended only after American companies transferred data on guidance systems, telemetry, aerodynamics and rocket failures.
In 1998, a congressional panel criticized satellite manufacturers for sometimes subordinating national security to the "bottom line" and concluded that their "illegally transmitted" information had improved the reliability of China's civilian and military rockets.
The next year the United States stopped permitting the use of American satellites for Chinese aerospace ventures amidst concerns about Chinese aid to missile programs in North Korea and Pakistan. China agreed in November 2000 not to assist other countries in developing ballistic missiles that could deliver nuclear weapons.
But the Central Intelligence Agency told Congress earlier this year that China has continued to provide missile-related items and/or assistance to North Korea and several other "countries of proliferation concerns."
The settlement ends a five-year federal investigation into how American satellite and aerospace companies aided China as they competed to have their satellites launched aboard Chinese rockets....Previously the Lockheed Martin Corp. and Loral Space and Communications Corp. agreed to pay fines - $13 million and $20 million respectively - to settle similar cases.
The Justice Department terminated its criminal investigation of Hughes and Loral last year without taking any action.... Officials said the $32 million civil penalty is the largest fine in an arms export case....The settlement also calls for the companies to appoint an outsider, a "separate third party," to monitor the agreement as well as future exports to countries such as China.
The latest agreement seems to disavow previous denials of wrongdoing by Hughes because it states that its "regret for not having obtained licenses that should have been obtained" was "notwithstanding Hughes' prior public comments to the contrary."...
|
Loral Submits Bankruptcy Exit Plan
Friday, August 20, 2004 - skyreport.com
Loral Space and Communications filed a plan of reorganization with the U.S. Bankruptcy Court in New York City Thursday, a proposal the company said is supported by a committee of unsecured creditors appointed in its chapter 11 case.
The plan, subject to confirmation by the bankruptcy court, resulted from negotiations between Loral and the creditors' committee, the company said.
Under the plan, Loral's two businesses, Space Systems/Loral and Loral Skynet, will emerge intact as separate subsidiaries of a reorganized Loral. Space Systems/Loral, the satellite design and manufacturing business, will emerge debt-free.
The common stock of the new Loral will be owned by Loral bondholders, Loral Orion bondholders and other unsecured creditors. In addition, bondholders and other creditors of Loral Orion will receive $200 million in notes that will be issued by the reorganized Loral Skynet, new Loral's satellite services subsidiary.
Loral said it will emerge from bankruptcy as a public company and will seek listing on a major stock exchange. Existing common and preferred stock will be cancelled and no distribution will be made to current shareholders, the company said.
Loral said it expects to exit chapter 11 under current management before the end of the year.
|
 see this [source pdf data]/div>
see this [source pdf data]/div>
 see this PDF [back-up] detailing APT (HK) Satellite / Loral [Bermuda/Asia]
see this PDF [back-up] detailing APT (HK) Satellite / Loral [Bermuda/Asia]
APT Satellite Company, is a Hong Kong-based consortium involving China Telecommunications Broadcast Satellite Corporation and other PRC companies, Ruentex Construction and Development of Taiwan, Telecom Holding Company of Thailand and Singapore Telecom, in the financing of the APSTAR satellites. - source
|
|
APSTAR VI is a high power satellite based on a SB-4100 C1 model with 38 C-band (64 W each) transponders and 12 Ku-band (145 W each) transponders. This satellite will have an Asia Pacific footprint including Hawaii and a mission life of over 14 years. Besides, it is the first civil satellite in China to be equipped with anti-jamming system.
APSTAR VI was launched on Apr 12, 2005 and replaced APSTAR IA at geostationary orbital slot 134 degree East on June 15, 2005.
|
|
Space Systems/Loral Awarded Contract to Build AsiaSat 5 Satellite
Palo Alto, CA - May 3, 2006 - www.ssloral.com
Space Systems/Loral (SS/L), a subsidiary of Loral Space & Communications (NASDAQ: LORL), today announced that it has been chosen by Asia Satellite Telecommunications Company Limited (AsiaSat), Hong Kong, to build AsiaSat 5, a new generation communications satellite designed to offer improved power and coverage to AsiaSat's customers across the Asia Pacific region.
"Space Systems/Loral has a well-established history of providing satellites for many of the premier operators in the Asia Pacific region," said Pat DeWitt, president, Space Systems/Loral. "We look forward to continuing that heritage by building this new addition to the AsiaSat fleet."
AsiaSat 5, a fixed satellite services (FSS) spacecraft expected to launch in 2008, will replace and expand upon the services provided by AsiaSat 2 at 100.5 degrees East longitude. The satellite will be based on SS/L's 1300 platform, which features qualified, flight proven subsystems and a long record of reliable operation.
"We selected SS/L to build the AsiaSat 5 satellite after a long evaluation and are very happy with the technology and value they provide to AsiaSat," said Peter Jackson, CEO, AsiaSat. "We are especially pleased with SS/L's record of building reliable and flexible satellites and its commitment to stand behind each product. We look forward to bringing to our customers in Asia the improved services this satellite will offer."
The satellite's payload will carry both C- and Ku-band transponders and has a 15-year mission life. AsiaSat 5 will be compatible with a range of commercial launch vehicles.
AsiaSat, the leading regional satellite operator in Asia, serves over two-thirds of the world's population with its three satellites, AsiaSat 2, AsiaSat 3S and AsiaSat 4. The AsiaSat satellite system provides services to both the broadcast and telecommunications industries. Over 240 digital television channels and 130 radio channels are now delivered by the company's satellites, reaching over 96 million households, with more than 360 million viewers across the Asia Pacific region. Many telecommunications customers use AsiaSat for services such as public telephone networks, private VSAT networks and high speed Internet and multimedia services. AsiaSat is a wholly owned subsidiary of Asia Satellite Telecommunications Holdings Limited, listed on both the Hong Kong (SEHK: 1135HK) and New York (NYSE: SAT) stock exchanges. For more information, please visit www.asiasat.com.
Space Systems/Loral is a premier designer, manufacturer, and integrator of powerful satellites and satellite systems. SS/L also provides a range of related services that include mission control operations and procurement of launch services. Based in Palo Alto, Calif., the company has an international base of commercial and governmental customers whose applications include broadband digital communications, direct-to-home broadcast, defense communications, environmental monitoring, and air traffic control. SS/L satellites have amassed more than 1,200 years of reliable on-orbit service. SS/L is ISO 9001:2000 certified. For more information, visit www.ssloral.com.
Loral Space & Communications is a high technology company that concentrates primarily on satellite manufacturing and satellite-based services. For more information, visit Loral's web site at www.loral.com.
|
AT&T octopus company in NSA spying Program
|
AT&T Deploys Government Spy Gear on WorldNet Network
-- 16 January, 2004
In 2003 AT&T built "secret rooms" hidden deep in the bowels of its central offices in various cities, housing computer gear for a government spy operation which taps into the company's popular WorldNet service and the entire internet. These installations enable the government to look at every individual message on the internet and analyze exactly what people are doing. Documents showing the hardwire installation in San Francisco suggest that there are similar locations being installed in numerous other cities.
The physical arrangement, the timing of its construction, the government-imposed secrecy surrounding it, and other factors all strongly suggest that its origins are rooted in the Defense Department's Total Information Awareness (TIA) program which brought forth vigorous protests from defenders of constitutionally protected civil liberties last year:
"As the director of the effort, Vice Adm. John M. Poindexter, has described the system in Pentagon documents and in speeches, it will provide intelligence analysts and law enforcement officials with instant access to information from internet mail and calling records to credit card and banking transactions and travel documents, without a search warrant." The New York Times, 9 November 2002
To mollify critics, the Defense Advanced Research Projects Agency (Darpa) spokesmen have repeatedly asserted that they are only conducting "research" using "artificial synthetic data" or information from "normal DOD intelligence channels" and hence there are "no U.S. citizen privacy implications" (Department of Defense, Office of the Inspector General report on TIA, December 12, 2003). They also changed the name of the program to "Terrorism Information Awareness" to make it more politically palatable. But feeling the heat, Congress made a big show of allegedly cutting off funding for TIA in late 2003, and the political fallout resulted in Adm. Poindexter's abrupt resignation last August. However, the fine print reveals that Congress eliminated funding only for "the majority of the TIA components," allowing several "components" to continue (DOD, ibid). The essential hardware elements of a TIA-type spy program are being surreptitiously slipped into "real world" telecommunications offices.
In San Francisco the "secret room" is Room 641A at 611 Folsom Street, the site of a large SBC phone building, three floors of which are occupied by AT&T. High-speed fiber-optic circuits come in on the 8th floor and run down to the 7th floor where they connect to routers for AT&T's WorldNet service, part of the latter's vital "Common Backbone." In order to snoop on these circuits, a special cabinet was installed and cabled to the "secret room" on the 6th floor to monitor the information going through the circuits. (The location code of the cabinet is 070177.04, which denotes the 7th floor, aisle 177 and bay 04.) The "secret room" itself is roughly 24-by-48 feet, containing perhaps a dozen cabinets including such equipment as Sun servers and two Juniper routers, plus an industrial-size air conditioner.
The normal work force of unionized technicians in the office are forbidden to enter the "secret room," which has a special combination lock on the main door. The telltale sign of an illicit government spy operation is the fact that only people with security clearance from the National Security Agency can enter this room. In practice this has meant that only one management-level technician works in there. Ironically, the one who set up the room was laid off in late 2003 in one of the company's endless "downsizings," but he was quickly replaced by another.
Plans for the "secret room" were fully drawn up by December 2002, curiously only four months after Darpa started awarding contracts for TIA. One 60-page document, identified as coming from "AT&T Labs Connectivity & Net Services" and authored by the labs' consultant Mathew F. Casamassima, is titled Study Group 3, LGX/Splitter Wiring, San Francisco and dated 12/10/02. (See sample PDF 1-4.) This document addresses the special problem of trying to spy on fiber-optic circuits. Unlike copper wire circuits which emit electromagnetic fields that can be tapped into without disturbing the circuits, fiber-optic circuits do not "leak" their light signals. In order to monitor such communications, one has to physically cut into the fiber somehow and divert a portion of the light signal to see the information.
This problem is solved with "splitters" which literally split off a percentage of the light signal so it can be examined. This is the purpose of the special cabinet referred to above: Circuits are connected into it, the light signal is split into two signals, one of which is diverted to the "secret room." The cabinet is totally unnecessary for the circuit to perform -- in fact it introduces problems since the signal level is reduced by the splitter -- its only purpose is to enable a third party to examine the data flowing between sender and recipient on the internet.
The above-referenced document includes a diagram (PDF 3) showing the splitting of the light signal, a portion of which is diverted to "SG3 Secure Room," i.e., the so-called "Study Group" spy room. Another page headlined "Cabinet Naming" (PDF 2) lists not only the "splitter" cabinet but also the equipment installed in the "SG3" room, including various Sun devices, and Juniper M40e and M160 "backbone" routers. PDF file 4 shows one of many tables detailing the connections between the "splitter" cabinet on the 7th floor (location 070177.04) and a cabinet in the "secret room" on the 6th floor (location 060903.01). Since the San Francisco "secret room" is numbered 3, the implication is that there are at least several more in other cities (Seattle, San Jose, Los Angeles and San Diego are some of the rumored locations), which likely are spread across the United States.
One of the devices in the "Cabinet Naming" list is particularly revealing as to the purpose of the "secret room": a Narus STA 6400. Narus is a 7-year-old company which, because of its particular niche, appeals not only to businessmen (it is backed by AT&T, JP Morgan and Intel, among others) but also to police, military and intelligence officials. Last November 13-14, for instance, Narus was the "Lead Sponsor" for a technical conference held in McLean, Virginia, titled "Intelligence Support Systems for Lawful Interception and Internet Surveillance." Police officials, FBI and DEA agents, and major telecommunications companies eager to cash in on the "war on terror" had gathered in the hometown of the CIA to discuss their special problems. Among the attendees were AT&T, BellSouth, MCI, Sprint and Verizon. Narus founder, Dr. Ori Cohen, gave a keynote speech. So what does the Narus STA 6400 do?
"The (Narus) STA Platform consists of stand-alone traffic analyzers that collect network and customer usage information in real time directly from the message.... These analyzers sit on the message pipe into the ISP (internet service provider) cloud rather than tap into each router or ISP device" (Telecommunications magazine, April 2000). A Narus press release (1 Dec., 1999) also boasts that its Semantic Traffic Analysis (STA) technology "captures comprehensive customer usage data ... and transforms it into actionable information.... (It) is the only technology that provides complete visibility for all internet applications."
To implement this scheme, WorldNet's high-speed data circuits already in service had to be rerouted to go through the special "splitter" cabinet. This was addressed in another document of 44 pages from AT&T Labs, titled "SIMS, Splitter Cut-In and Test Procedure," dated 01/13/03 (PDF 5-6). "SIMS" is an unexplained reference to the secret room. Part of this reads as follows:
"A WMS (work) Ticket will be issued by the AT&T Bridgeton Network Operation Center (NOC) to charge time for performing the work described in this procedure document....
"This procedure covers the steps required to insert optical splitters into select live Common Backbone (CBB) OC3, OC12 and OC48 optical circuits."
The NOC referred to is in Bridgeton, Missouri, and controls WorldNet operations. (As a sign that government spying goes hand-in-hand with union-busting, the entire (Communication Workers of America) Local 6377 which had jurisdiction over the Bridgeton NOC was wiped out in early 2002 when AT&T fired the union work force and later rehired them as nonunion "management" employees.) The cut-in work was performed in 2003, and since then new circuits are connected through the "splitter" cabinet.
Another "Cut-In and Test Procedure" document dated January 24, 2003, provides diagrams of how AT&T Core Network circuits were to be run through the "splitter" cabinet (PDF 7). One page lists the circuit IDs of key Peering Links which were "cut-in" in February 2003 (PDF 8), including ConXion, Verio, XO, Genuity, Qwest, PAIX, Allegiance, AboveNet, Global Crossing, C&W, UUNET, Level 3, Sprint, Telia, PSINet and Mae West. By the way, Mae West is one of two key internet nodal points in the United States (the other, Mae East, is in Vienna, Virginia). It's not just WorldNet customers who are being spied on -- it's the entire internet.
The next logical question is, what central command is collecting the data sent by the various "secret rooms"? One can only make educated guesses, but perhaps the answer was inadvertently given in the DOD Inspector General's report (cited above):
"For testing TIA capabilities, Darpa and the U.S. Army Intelligence and Security Command (INSCOM) created an operational research and development environment that uses real-time feedback. The main node of TIA is located at INSCOM (in Fort Belvoir, Virginia)…."
Among the agencies participating or planning to participate in the INSCOM "testing" are the "National Security Agency, the Defense Intelligence Agency, the Central Intelligence Agency, the DOD Counterintelligence Field Activity, the U.S. Strategic Command, the Special Operations Command, the Joint Forces Command and the Joint Warfare Analysis Center." There are also "discussions" going on to bring in "non-DOD federal agencies" such as the FBI.
This is the infrastructure for an Orwellian police state. It must be shut down!
|
Spying programs and manipulation
of the public via data systems is nothing new
|
ChoicePoint
ChoicePoint is an Alpharetta, Georgia-based company that sells information in three markets--insurance, business and government, and marketing. According to a recent quarterly statement filed at the Security and Exchange Commission, ChoicePoint sells: "claims history data, motor vehicle records, police records, credit information and modeling services...employment background screenings and drug testing administration services, public record searches, vital record services, credential verification, due diligence information, Uniform Commercial Code searches and filings, DNA identification services, authentication services and people and shareholder locator information searches...print fulfillment, teleservices, database and campaign management services..."
ChoicePoint has managed to attain a large share of the commercial data broker (CDB) market with strategic purchases of other businesses. Since its spinoff from Equifax in 1997, ChoicePoint has acquired a number of information collection and processing companies. These include:
National Data Retrieval, Inc., a provider of public records information; List Source, Inc., d/b/a Kramer Lead Marketing Group, a marketing company in the life and health insurance and financial services markets; Mortgage Asset Research Institute, Inc., a mortgage fraud monitoring company; Identico Systems, LLC, a customer identity verification company; Templar Corporation; insuranceDecisions, Inc., an insurance industry claims administration company; Bridger Systems, Inc., a USA PATRIOT Act compliance company; CITI NETWORK, Inc. d/b/a Applicant Screening and Processing, a tenant screening company; TML Information Services, Inc., a provider of motor vehicle reports; Drug Free, Inc., a drug testing company; National Drug Testing, Inc., a drug testing company; Application Profiles, Inc., a background check company; Informus Corporation; a company enabling ChoicePoint to offer products online; Tyler-McLennon, Inc., a background screening company; ChoicePoint Direct Inc., formerly known as Customer Development Corporation, a database marketing company; EquiSearch Services, Inc.; DATEQ Information Network, Inc., an insurance underwriting services company; Washington Document Service, Inc., a court record retrieval service; DataTracks Technology, Inc., a public record information company; DataMart, Inc., a database software company; Statewide Data Services, Inc; NSA Resources, Inc., a drug testing company; DBT Online, Inc., a public record services provider; RRS Police Records Management, Inc., a provider of police reports and related services; VIS'N Service Corporation; Cat Data Group, LLC; Drug Free Consortium, a drug testing company; BTi Employee Screening Services, Inc., an employee pre-screening services company; ABI Consulting Inc., a drug screening company; Insurity Solutions, Inc., an insurance rating company; National Medical Review Offices, Inc.; Bode Technology Group, Inc., a DNA identification company; Marketing Information & Technology, Inc., a direct marketing company; Pinkerton's, Inc., a preemployment screening company; Total eData Corporation, an e-mail database company; L&S Report Service, Inc., a provider of police records; Resident Data, Inc., a residential screening services provider; Vital Chek Network, Inc., a provider of vital records; Accident Report Services, Inc., a provider of police records; Programming Resources Company, insurance software company; Professional Test Administrators, Inc., a drug testing company; CDB Infotek, a seller of public records; Medical Information Network, LLC, an online physician verification service; and Rapsheets.com, an online provider of criminal records data.
An April 13, 2001 article in the Wall Street Journal reported that profiling company ChoicePoint provided personal information to at least thirty-five government agencies. EPIC has filed a series of Freedom of Information Act requests to determine the nature and amount of information sold to government. To date, EPIC has determined that ChoicePoint has several multi-million dollar contracts with law enforcement agencies to sell personal data.
ChoicePoint sells a wide array of information to the government, including:
Credit headers, a list of identifying information that appears at the top of a credit report. This information includes name, spouse's name, address, previous address, phone number, Social Security number, and employer.
"Workplace Solutions Pre-Employment Screening," which includes financial reports, education verification, reference verification, felony check, motor vehicle record, SSN verification, and professional credential verification.
Asset Location Services.
The ability to engage in "wildcard searches," which allows law enforcement to "obtain a comprehensive personal profile in a matter of minutes" with only a first name or partial address.
The use of "Soundex" queries, which allow searches on personal information based on how names sound, rather than how they are spelled.
Information on neighbors and family members of a suspect.
ChoicePoint's AutoTrackXP is one of the most favored CDB products. It provides an interface for additional data points, including:
Linkage services, which draw graphical relationships between suspects and other addresses, neighbors, and Social Security Numbers.
Public records, including Social Security Death Master Filings, bookings and arrests, liens, judgments, and bankruptcies.
Licenses, including drivers, pilots, and professional credentials.
Lists of residents of Georgia, New York, and Ohio.
National real-time phone directories and reverse look up services.
Business information, compiled nationwide from Secretaries of State.
"SmartSeach," a tool that allows broad wildcard searches: "There may be thousands of Jane Does, but there's probably only one Jane Doe who's between 25 and 30 and lives on the upper west side of Manhattan. SmartSearch makes it possible to find that one."
U.S. Military Personnel.
Boat owners.
much more from the Electronic Privacy Info Center
|
Data mining & Data tampering...The Politics of Tyranny in action
|
Florida's flawed "voter-cleansing" program
Secretary of State Katherine Harris hired a firm to vet the rolls for felons, but that may have wrongly kept thousands, particularly blacks, from casting ballots.
By Gregory Palast Dec. 4, 2000 | salon.com
If Vice President Al Gore is wondering where his Florida votes went, rather than sift through a pile of chad, he might want to look at a "scrub list" of 173,000 names targeted to be knocked off the Florida voter registry by a division of the office of Florida Secretary of State Katherine Harris. A close examination suggests thousands of voters may have lost their right to vote based on a flaw-ridden list that included purported "felons" provided by a private firm with tight Republican ties.
Early in the year, the company, ChoicePoint, gave Florida officials a list with the names of 8,000 ex-felons to "scrub" from their list of voters. But it turns out none on the list were guilty of felonies, only misdemeanors. The company acknowledged the error, and blamed it on the original source of the list -- the state of Texas.
Florida officials moved to put those falsely accused by Texas back on voter rolls before the election. Nevertheless, the large number of errors uncovered in individual counties suggests that thousands of eligible voters may have been turned away at the polls.
Florida is the only state that pays a private company that promises to "cleanse" voter rolls.The state signed in 1998 a $4 million contract with DBT Online, since merged into ChoicePoint, of Atlanta. The creation of the scrub list, called the central voter file, was mandated by a 1998 state voter fraud law, which followed a tumultuous year that saw Miami's mayor removed after voter fraud in the election, with dead people discovered to have cast ballots. The voter fraud law required all 67 counties to purge voter registries of duplicate registrations, deceased voters and felons, many of whom, but not all, are barred from voting in Florida.
In the process, however, the list invariably targets a minority population in Florida, where 31 percent of all black men cannot vote because of a ban on felons. In compiling a list by looking at felons from other states, Florida could, in the process, single out citizens who committed felons in other states but, after serving their time or successfully petitioning the courts, had their voting rights returned to them. According to Florida law, felons can vote once their voting rights have been reinstated.
And if this unfairly singled out minorities, it unfairly handicapped Gore: In Florida, 93 percent of African-Americans voted for the vice president.
In the 10 counties contacted by Salon, use of the central voter file seemed to vary wildly. Some found the list too unreliable and didn't use it at all. But most counties appear to have used the file as a resource to purge names from their voter rolls, with some counties making little -- or no -- effort at all to alert the "purged" voters. Counties that did their best to vet the file discovered a high level of errors, with as many as 15 percent of names incorrectly identified as felons.
News coverage has focused on some maverick Florida counties that decided not to use the central voter file, essentially breaking the law and possibly letting some ineligible felons vote. On Friday, the Miami Herald reported that after researching voter records in 12 Florida counties -- but primarily in Palm Beach and Duval counties, which didn't use the file -- it found that more than 445 felons had apparently cast ballots in the presidential election.
But Palm Beach and Duval weren't the only counties to dump the list after questioning its accuracy. Madison County's elections supervisor, Linda Howell, had a peculiarly personal reason for distrusting the central voter file: She had received a letter saying that since she had committed a felony, she would not be allowed to vote.
Howell, who said she has never committed a felony, said the letter she received in March shook her faith in the process. "It really is a mess," she said.
"I was very upset," Howell said. "I know I'm not a felon." Though the mistake did get corrected and law enforcement officials were quite apologetic, Howell decided not to use the state list anymore because its "information is so flawed." She's unsure of the number of warning letters that were sent out to county residents when she first received the list in 1999, but she recalls that there were many problems. "One day we would send a letter to have someone taken off the rolls, and the next day, we would send one to put them back on again," Howell said. "It makes you look like you must be a dummy."
Dixie and Washington counties also refused to use the scrub lists. Starlet Cannon, Dixie's deputy assistant supervisor of elections, said, "I'm scared to work with it because of lot of the information they have on there is not accurate." Carol Griffin, supervisor of elections for Washington, said, "It hasn't been accurate in the past, so we had no reason to suspect it was accurate this year."
But if some counties refused to use the list altogether, others seemed to embrace it all too enthusiastically. Etta Rosado, spokeswoman for the Volusia County Department of Elections, said the county essentially accepted the file at face value, did nothing to confirm the accuracy of it and doesn't inform citizens ahead of time that they have been dropped from the voter rolls.
"When we get the con felon list, we automatically start going through our rolls on the computer. If there's a name that says John Smith was convicted of a felony, then we enter a notation on our computer that says convicted felon -- we mark an "f" for felon -- and the date that we received it," Rosado said. "They're still on our computer, but they're on purge status," meaning they have been marked ineligible to vote.
"I don't think that it's up to us to tell them they're a convicted felon," Rosado said. "If he's on our rolls, we make a notation on there. If they show up at a polling place, we'll say, 'Wait a minute, you're a convicted felon, you can't vote. Nine out of 10 times when we repeat that to the person, they say 'Thank you' and walk away. They don't put up arguments." Rosado doesn't know how many people in Volusia were dropped from the list as a result of being identified as felons.
Hillsborough County's elections supervisor, Pam Iorio, tried to make sure that that the bugs in the system didn't keep anyone from voting. All 3,258 county residents who were identified as possible felons on the central voter file sent by the state in June were sent a certified letter informing them that their voting rights were in jeopardy. Of that number, 551 appealed their status, and 245 of those appeals were successful. Some had been convicted of a misdemeanor and not a felony, others were felons who had had their rights restored and others were simply cases of mistaken identity.
An additional 279 were not close matches with names on the county's own voter rolls and were not notified. Of the 3,258 names on the original list, therefore, the county concluded that more than 15 percent were in error. If that ratio held statewide, no fewer than 7,000 voters were incorrectly targeted for removal from voting rosters.
Iorio says local officials did not get adequate preparation for purging felons from their rolls. "We're not used to dealing with issues of criminal justice or ascertaining who has a felony conviction," she said. Though the central voter file was supposed to facilitate the process, it was often more troublesome than the monthly circuit court lists that she had previously used to clear her rolls of duplicate registrations, the deceased and convicted felons. "The database from the state level is not always accurate," Iorio said. As a consequence, her county did its best to notify citizens who were on the list about their felony status. "We sent those individuals a certified letter, we put an ad in a local newspaper and we held a public hearing. For those who didn't respond to that, we sent out another letter by regular mail," Iorio said. "That process lasted several months."
"We did run some number stats and the number of blacks [on the list] was higher than expected for our population," says Chuck Smith, a statistician for the county. Iorio acknowledged that African-Americans made up 54 percent of the people on the original felons list, though they constitute only 11.6 percent of Hillsborough's voting population.
Smith added that the DBT computer program automatically transformed various forms of a single name. In one case, a voter named "Christine" was identified as a felon based on the conviction of a "Christopher" with the same last name. Smith says ChoicePoint would not respond to queries about its proprietary methods. Nor would the company provide additional verification data to back its fingering certain individuals in the registry purge. One supposed felon on the ChoicePoint list is a local judge.
While there was much about the lists that bothered Iorio, she felt she didn't have a choice but to use them. And she's right. Section 98.0975 of the Florida Constitution states:
"Upon receiving the list from the division, the supervisor must attempt to verify the information provided. If the supervisor does not determine that the information provided by the division is incorrect, the supervisor must remove from the registration books by the next subsequent election the name of any person who is deceased, convicted of a felony or adjudicated mentally incapacitated with respect to voting."
But the counties have interpreted that law in different ways. Leon County used the central voter file sent in January 2000 to clean up its voter rolls, but set aside the one it received in July. According to Thomas James, the information systems officer in the county election office, the list came too late for the information to be processed.
According to Leon election supervisor Ion Sancho, "there have been some problems" with the file. Using the information received in January, Sancho sent 200 letters to county voters, by regular mail, telling them they had been identified by the state as having committed a felony and would not be allowed to vote. They were given 30 days to respond if there was an error. "They had the burden of proof," he says. He says 20 people proved that they did not belong on the list, and a handful of angry phone calls followed on Election Day. "Some people threatened to sue us," he said, "but we haven't had any lawyers calling yet."
In Orange County, officials also sent letters to those identified as felons by the state, but they appear to have taken little care in their handling of the list. "I have no idea," said June Condrun, Orange's deputy supervisor of elections, when asked how many letters were sent out to voters. After a bit more thought, Condrun responded that "several hundred" of the letters were sent, but said she doesn't know how many people complained. Those who did call, she said, were given the phone number of the Florida Department of Law Enforcement so that they could appeal directly to it.
Many Orange County voters never got the chance to appeal in any form. Condrun noted that about one-third of the letters, which the county sent out by regular mail, were returned to the office marked undeliverable. She attributed the high rate of incorrect addresses to the age of the information sent by DBT, some of which was close to 20 years old, she said.
Miami-Dade County officials may have had similar trouble. Milton Collins, assistant supervisor of elections, said he isn't comfortable estimating how many accused felons were identified by the central voter file in his county. He said he knows that about 6,000 were notified, by regular mail, about an early list in 1999. Exactly how many were purged from the list? "I honestly couldn't tell you," he said. According to Collins, the most recent list he received from the state was one sent in January 2000, and the county applied a "two-pass system": If the information on the state list seemed accurate enough when comparing names with those on county voter lists, people were classified as felons and were then sent warning letters. Those who seemed to have only a partial match with the state data were granted "temporary inactive status." Both groups of people were given 90 days to respond or have their names struck from the rolls.
But Collins said the county has no figures for how many voters were able to successfully appeal their designation as felons.
ChoicePoint spokesman Martin Fagan concedes his company's error in passing on the bogus list from Texas. ("I guess that's a little bit embarrassing in light of the election," he says.) He defends the company's overall performance, however, dismissing the errors in 8,000 names as "a minor glitch -- less than one-tenth of 1 percent of the electorate" (though the total equals 15 times Gov. George W. Bush's claimed lead over Gore). But he added that ChoicePoint is responsible only for turning over its raw list, which is then up to Florida officials to test and correct.
Last year, DBT Online, with which ChoicePoint would soon merge, received the unprecedented contract from the state of Florida to "cleanse" registration lists of ineligible voters -- using information gathering and matching criteria it has refused to disclose, even to local election officials in Florida.
Atlanta's ChoicePoint, a highflying dot-com specializing in sales of personal information gleaned from its database of 4 billion public and not-so-public records, has come under fire for misuse of private data from government computers. In January, the state of Pennsylvania terminated a contract with ChoicePoint after discovering the firm had sold citizens' personal profiles to unauthorized individuals.
Fagan says many errors could have been eliminated by matching the Social Security numbers of ex-felons on DBT lists to the Social Security numbers on voter registries. However, Florida's counties have Social Security numbers on only a fraction of their voter records. So with those two problems -- Social Security numbers missing in both the DBT's records and the counties' records -- that fail-safe check simply did not exist.
In its defense, the company proudly points to an award it received from Voter Integrity Inc. on April 1 for "innovative excellence [in] cleansing" Florida voter rolls. The conservative, nonprofit advocacy organization has campaigned in parallel with the Republican Party against the 1993 motor voter law that resulted in a nationwide increase in voter registration of 7 million, much of it among minority voters. DBT Online partnered with Voter Integrity Inc. three days later, setting up a program to let small counties "scrub" their voting lists, too.
Florida is the only state in the nation to contract the first stage of removal of voting rights to a private company. And ChoicePoint has big plans. "Given the outcome of our work in Florida," says Fagan, "and with a new president in place, we think our services will expand across the country."
Especially if that president is named "Bush." ChoicePoint's board and executive roster are packed with Republican stars, including billionaire Ken Langone, a company director who was chairman of the fund-raising committee for New York Mayor Rudy Giuliani's aborted run against Hillary Rodham Clinton. Langone is joined at ChoicePoint by another Giuliani associate, former New York Police Commissioner Howard Safir. And Republican power lobbyist and former congressman Vin Weber lobbies for ChoicePoint in Washington. Just before his death in 1998, Rick Rozar, president of a Choicepoint company, CDB Infotek, donated $100,000 to the Republican Party.
(Alicia Montgomery, Daryl Lindsey and Anthony York contributed to this story.)
|
Who Won the War on Iraq?
The Carlyle Group,
Lockheed Martin, Choice Point - and more
by
Greg Palast
Greg Palast investigative reporter and
author of The Best Democracy Money Can Buy answered that question at his
April 28, 2003 stop in Berkeley, CA. Was it the Carlyle Group, Barrick Gold, or
Lockheed? - or all of the above?
Greg Palast, whose films, books and
articles have a huge and devoted audience in Europe can't get his work shown or
printed in the mass media in the US where he was born. Visit: www.gregpalast.com
His friend, Jello Biafra, the lead singer
of the band The Dead Kenndys, offers an explanation why that is so. He introduced
Palast to a standing room audience at Cody's books in Berkeley.
|
Seg
|
Title
|
Length
|
File
Info
|
Download
|
Play
|
|
1
|
Part One of Two
|
29:00
|
48 kbps MP3 (9.96 MB)
|
FTP
HTTP
|
Play
|
|
2
|
Part Two of Two
|
29:00
|
48 kbps MP3 (9.96 MB)
|
FTP
HTTP
|
Play
|
|
Update: THE SPIES WHO SHAG US
The Times and USA Today have Missed the Bigger Story -- Again
Buzzflash - Friday, May 12, 2006 by Greg Palast
I know you're shocked -- SHOCKED! -- that George Bush is listening in on all your phone calls. Without a warrant. That's nothing. And it's not news.
This is: the snooping into your phone bill is just the snout of the pig of a strange, lucrative link-up between the Administration's Homeland Security spy network and private companies operating beyond the reach of the laws meant to protect us from our government. You can call it the privatization of the FBI -- though it is better described as the creation of a private KGB.
The leader in the field of what is called "data mining," is a company called, "ChoicePoint, Inc," which has sucked up over a billion dollars in national security contracts.
Worried about Dick Cheney listening in Sunday on your call to Mom? That ain't nothing. You should be more concerned that they are linking this info to your medical records, your bill purchases and your entire personal profile including, not incidentally, your voting registration. Five years ago, I discovered that ChoicePoint had already gathered 16 billion data files on Americans -- and I know they've expanded their ops at an explosive rate.
They are paid to keep an eye on you -- because the FBI can't. For the government to collect this stuff is against the law unless you're suspected of a crime. (The law in question is the Constitution.) But ChoicePoint can collect it for "commercial" purchases -- and under the Bush Administration's suspect reading of the Patriot Act -- our domestic spying apparatchiks can then BUY the info from ChoicePoint.
Who ARE these guys selling George Bush a piece of you?
ChoicePoint's board has more Republicans than a Palm Beach country club. It was funded, and its board stocked, by such Republican sugar daddies as billionaires Bernie Marcus and Ken Langone -- even after Langone was charged by the Securities Exchange Commission with abuse of inside information.
I first ran across these guys in 2000 in Florida when our Guardian/BBC team discovered the list of 94,000 "felons" that Katherine Harris had ordered removed from Florida's voter rolls before the election. Virtually every voter purged was innocent of any crime except, in most cases, Voting While Black. Who came up with this electoral hit list that gave Bush the White House? ChoicePoint, Inc.
And worse, they KNEW the racially-tainted list of felons was bogus. And when we caught them, they lied about it. While they've since apologized to the NAACP, ChoicePoint's ethnic cleansing of voter rolls has been amply rewarded by the man the company elected.
And now ChoicePoint and George Bush want your blood. Forget your phone bill. ChoicePoint, a sickened executive of the company told us in confidence, "hope[s] to build a database of DNA samples from every person in the United States ...linked to all the other information held by CP [ChoicePoint]" from medical to voting records.
And ChoicePoint lied about that too. The company publicly denied they gave DNA to the Feds -- but then told our investigator, pretending to seek work, that ChoicePoint was "the number one" provider of DNA info to the FBI.
"And that scares the hell out of me," said the executive (who has since left the company), because ChoicePoint gets it WRONG so often. We are not contracting out our Homeland Security to James Bond here. It's more like Austin Powers, Inc. Besides the 97% error rate in finding Florida "felons," Illinois State Police fired the company after discovering ChoicePoint had produced test "results" on rape case evidence ... that didn't exist. And ChoicePoint just got hit with the largest fine in Federal Trade Commission history for letting identity thieves purchase 145,000 credit card records.
But it won't stop, despite Republican senators shedding big crocodile tears about "surveillance" of innocent Americans. That's because FEAR is a lucrative business -- not just for ChoicePoint, but for firms such as Syntech, Sybase and Lockheed-Martin -- each of which has provided lucrative posts or profits to connected Republicans including former Total Information Awareness chief John Poindexter (Syntech), Marvin Bush (Sybase) and Lynn Cheney (Lockheed-Martin).
But how can they get Americans to give up our personal files, our phone logs, our DNA and our rights? Easy. Fear sells better than sex -- and they want you to be afraid. Back to today's New York Times, page 28: "Wider Use of DNA Lists is Urged in Fighting Crime." And who is providing the technology? It comes, says the Times, from the work done on using DNA fragments to identity victims of the September 11 attack. And who did that job (for $12 million, no bid)? ChoicePoint, Inc. Which is NOT mentioned by the Times.
"Genetic surveillance would thus shift from the individual [the alleged criminal] to the family," says the Times -- which will require, of course, a national DNA database of NON-criminals.
It doesn't end there. Turn to the same newspaper, page 23, with a story about a weird new law passed by the state of Georgia to fight illegal immigration. Every single employer and government agency will be required to match citizen or worker data against national databases to affirm citizenship. It won't stop illegal border crossing, but hey, someone's going to make big bucks on selling data. And guess what local boy owns the data mine? ChoicePoint, Inc., of Alpharetta, Georgia.
The knuckleheads at the Times don't put the three stories together because the real players aren't in the press releases their reporters re-write.
But that's the Fear Industry for you. You aren't safer from terrorists or criminals or "felon" voters. But the national wallet is several billion dollars lighter and the Bill of Rights is a couple amendments shorter.
And that's their program. They get the data mine -- and we get the shaft.
|
|
"...ChoicePoint CEO Derek Smith has had a business association with Edward J. Mathias, a founder and managing director of the Carlyle group, and a director of its Asia Ventures Partners -- the subsidiary that has employed George H.W. "Poppy" Bush. Smith, Mathias, and ChoicePoint board member Bernard Marcus are all on the advisory board of the Yale University Chief Executive Leadership Institute (CELI). All three participated in the CELI May 2000 conference, somewhat ominously titled "Knowing Enough to Be Dangerous." Smith and Mathias both participated in a session titled "Knowing Too Much about the Customer: Responsible Uses of Information and When to Just Say No." In the 2001 CELI conference, titled "2001: What HAL Didn't Know," Mathias and Smith participated in a session titled, "Who Is Really Your Business Partner? What More Does HAL Need to Know about Us?"
The Privatization of Big Brother
very interesting Daily Kos thread
|
|
BIG BROTHER INC. TRIES TO FOOL RANDI RHODES -- AND THAT'S NOT NICE
Buzzflash Wednesday, May 17, 2006 by Greg Palast
I smell mendacity! The sticky-sweet Atlanta drawl of the PR flack for America's private KGB was dancing in rhetorical circles with Randi Rhodes, Air American, broadcast yesterday.. Unfortunately for the Bush-friendly Spies-R-Us contractor, Randi also has a keen nose for the telltale scent of pure bullshit.
By "private KGB," I mean ChoicePoint, Inc., the Atlanta company that keeps over 16 billion records on Americans which it sells to the FBI, Homeland Security and, through a bit of a slip-up, identity thieves.
They are watching you because George and Dick don't have time to track everyone in America (and that would be illegal, to boot), ChoicePoint does it. Then turns over the electronic you -- cross-matched profiles of voting registration, your DNA info and who knows what else -- for a price.
Randi was on the phone to one James Lee, Marketing Director of ChoicePoint. He was trying to explain some of the good work they do for government -- and responding to the evil lies about his corporation by a reporter (me).
I was listening in from a glass booth. The Eichmann treatment was required by ChoicePoint -- they wouldn't let her interview the company if anyone else was in the room. They also warned her, her interview would be "taped" ... AND, they didn't have to add, they know where she lives -- and where she votes and a whole lot more about Randi that maybe Randi herself doesn't know. Just a friendly warning.
It seems the data guys were upset that she had me on her show on Monday to talk about my investigations of the company which I conducted for BBC-TV, for Harper's and for my new book, Armed Madhouse. [Yeah, that's a plug: order it here.]
The company's name came up because of the Bush regime's getting caught with their hands in the data jar: spying on Americans, sucking our phone records into data bases where George and Dick can peruse them at leisure, without warrants.
ChoicePoint's the big banana in the data game, with fat no-bid contracts with Big Brother Bush's agency and the Department of Fatherland Security. (Homeland? Deutschland? Whatever.) Other governments, including Mexico, threatened ChoicePoint operatives with arrest for their use and misuse of data, but Dick and George like'm just fine. That's because ChoicePoint provides just the data that suits their needs -- not necessarily accurate, but accurate is not what is needed.
For example, ChoicePoint is the company that gave Katherine Harris and Jeb Bush the list of Florida voters, most of them Black, which were removed as "felons" before the 2000 election. The list was ridiculously inaccurate -- these were innocent citizens -- but those African-Americans lost their voting rights anyway and Jeb's brother thereby took the White House.
That's not nice, what Jeb and Katherine did -- but ChoicePoint kept silent. In return, they received a high, and highly suspect, fee for their "work."
And that's dangerous. Because, after ChoicePoint selected our president for us, our president selected them for no-bid jobs to save us from terrorists -- which they do by keeping track of us. (Odd, I thought Americans were the VICTIMS of terror -- they've made us the SUSPECTS.)
In Armed Madhouse, I reveal that one ChoicePoint executive confidentially told me the company's chairman hoped to build a national DNA database. Dracula's got nothing on these guys: they are already the biggest providers of DNA info to the FBI, they boast. They boast about it one week -- then they deny it another. This week's flavor is denial.
Back to Randi. I wasn't allowed in the room with her, so I waited in the glass booth. ChoicePoint had a huge list of complaints about my latest comment on their activities. I thought it important for the public to know how these private "data mining" companies drill into you and sell up the valuable nuggets they find to Mr. Bush's spy apparatus.
As a public service -- everyone needs a laugh once in a while -- I'm reprinting their inventive rebuttal to my report, "The Spies Who Shag Us"
The company uses some clever rhetorical sleights of hand: "No data files or 'dossiers' exist at ChoicePoint." Now that's just darn strange for a data company.
But that's a quibble. Let's move to the out and out flaming fabrications, whoppers and what, before George Bush took office, we used to call "stinking, bald-faced lies." (Now we call it, "intelligence.")
ChoicePoint swore to Ms. Rhodes that they do not have or sell "credit" information. Yet, according to the company's own filing, among their other Big Brother products, they sell:
"...claims history data, motor vehicle records, police records, CREDIT INFORMATION and modeling services...employment background screenings and drug testing administration services, public record searches, vital record services, credential verification, due diligence information, DNA identification services, authentication services and people and shareholder locator information searches...print fulfillment, teleservices, database and campaign management services..."
Uh, oh. They are either fibbing to the Securities and Exchange Commission (their CEO is already under investigation by the SEC) -- or they are prevaricating to Randi. They shouldn't do that, because, the lady has class -- she let ChoicePoint give their goofy alibi uninterrupted; but, lie to her, and, as my editor says, "she'll bite off a chicken's head while it's laying eggs."
So who are you toying with, Mr. ChoicePoint, the SEC or Randi?
There's more. ChoicePoint's PR apologist says it doesn't maintain credit card records, but they fail to mention that they sell "credit report headers" -- which is why the federal government just fined them a record $10 million for letting identity thieves run off with this kind of info. They sell "SSN verification" (your social security number), financial reports, education verification, reference verification, felony checks, motor vehicle records, asset location and information on criminal suspects and their neighbors and relatives. Howdy, neighbor!
Let's go back to ChoicePoint's dirty work for the Brothers Bush. ChoicePoint writes that it didn't get its corporate hands dirty in the racist purge of voters which fixed the 2000 election. That was the fault of some company called "DBT" which ChoicePoint only purchased, they claim, "after DBT's work was done for the state."
Au contraire. ChoicePoint bought DBT before the election, while the purges were in full swing. Then, right after the "election," ChoicePoint's PR mouthpieces boasted about how the company was going to cash in on its "success" (their word) in purging Florida voter rolls. Their PR flack told me at the time, "Given the outcome of our work in Florida, and with a new president in place (!), we think our services will expand across the country." But then we caught them -- and they quit elections games and moved on to saving us from Al Qaeda. Lord help us.
Frankly, my dear, I don't give a damn about ChoicePoint. They're in it for the money. If they turned a blind eye to evil, if they abetted the theft of an election and kept silent to keep the money, well, that's the Fear Industry for you.
It's not what ChoicePoint sells that terrifies me, it's whom they're selling it to: a regime for whom information is a weapon and disinformation a way of life.
|
|
they've had nearly 10 years to perfect this:
The people of Hong Kong were the guinea pigs...
Take a wild guess at what it's called!
|
| OCTOPUS SYSTEM - Hong Kong 1997
The Octopus Card, the first card employing FeliCa technology, was introduced in Hong Kong back in 1997. Today, over 12 million cards are in circulation, making Hong Kong one of the world's leading nations with extensive history in employing an automatic payment system in form of a contactless IC card.
The Octopus Card was initially used as a payment system for public transport such as the bus, metro, ferry boat and light rail. However, the services have greatly expanded for use in addition to public transport, today. Now, it can be used to pay for purchases at a convenience stores, fast food stores, and vending machines. The card also serves as employee ID, student ID and other ID cards, and has grown into a major choice for office entry/exit control, parking area entry/exit control and various other scenes. Simply put, the Octopus Card featuring FeliCa technology providing multi-application use, has grown into a modern and indispensable daily item.
|
|
|
The major characteristic of FeliCa is that it can be applied for items regardless of shape, as long as the application comes with a FeliCa IC chip and antenna. As result, many products are becoming a focus of interest. This can be witnessed with the wristwatch called the "Octopus Watch" and keyholders that are incorporating the FeliCa module.
sony.net
e-Payment with FeliCa Technology
Use of "Edy" a form of e-money applying FeliCa technology is also on the rise.*1
Edy can be used at any Edy member store presenting the Edy mark. This means Edy users can pay for their purchases at major convenience stores, major shopping complexes and even vending machines with an Edy mark. Edy is also an advantage for the store since it simplifies the payment registering process, unlike time consuming payments with coins.
Payment of the charges can be easily be made from a payment reader that is setup in the store, as well as over the Internet by connecting "PaSoRi" (USB Reader/Writer)to a PC.*2
By using "eLIO", users can safely pay for items over the internet since there is no need to input a credit number for every payment.*3
sony.net
|
FeliCa [sony] - KDDI = Carlye
|
KDDI, one of the three major mobile carriers in Japan, will soon introduce wallet phones (you can call them EZ FeliCa-compliant handsets if you like lengthy names). It is basically the same thing as what NTT DoCoMo introduced last summer. Two new KDDI/au handsets (W32S and W32H) having embedded FeliCa RFID chips will be introduced this September. Users of these handsets will likely be able to use mobile SUICA service (the service that allows people to use mobile phones as RFID train passes) as well in January 2006. Until then, they will be just good old wallet phones.
ubiks.net/l
|
|
Carlyle Group Buys Part Of KDDI
Japanese mobile carrier KDDI has been trying to sell their DDI Pocket division for many months (leading to the inevitable joke/question of whether or not KDDI minus DDI will be simply known as "K"?).
DDI Pocket offers the personal handyphone system, which is popular in Japan. It's sort of a cheap approximation of a mobile phone system, but has found new life in supplying wireless data access to Japanese users. The expected buyer from the beginning of all this talk has always been Kyocera, who already owned a small piece of DDI pocket.
Despite denials, it looks like Kyocera is buying up DDI pocket, but they've brought in quite the powerhouse partner - which will actually make them the smaller player in the deal. The Carlyle Group has announced that they'll be teaming up with Kyocera to buy DDI Pocket.
The Carlyle Group, of course, is known for hiring up big shot political insiders and other world leaders (such as Lou Gerstner) so they certainly have a few connections up their sleeves.
They'll now own 60% of the firm and apparently are looking to bring the technology to developing countries that might not have the infrastructure for a full mobile phone system, but could find the PHS system useful.
KDDI, in the meantime, will focus on their real mobile phone market in Japan, which was starting to eat into the DDI Pocket market anyway. It's an interesting look at how a technology that is becoming obsolete in an advanced society could present huge opportunities for developing nations instead. As the second link above shows, this also shows how Japanese firms are increasingly open to being bought by foreign firms -- something that's been rare in the past (though, Ripplewood's buyout of J-Phone's landline business in Japan suggests a trend).
- techdirt.com
|
|
Sony and NTT DoCoMo Agree to Form Joint Venture Company for FeliCa Business Partnerships
- Creating a New Lifestyle Based on the Open FeliCa Platform -
TOKYO, JAPAN, October 27, 2003 ---
Sony Corporation and
NTT DoCoMo, Inc. have agreed to form a Joint Venture Company to develop new services based on mobile phones equipped with Sony's contactless IC Card technology FeliCa®. The Joint Venture is targeted for establishment in January 2004. Discussions between Sony and DoCoMo will continue to finalize the details of this company which will be named: FeliCa Networks, Inc.
Sony began developing FeliCa in 1988, and business use of the technology became widespread following the deployment of the technology in Hong Kong transport systems in 1997. FeliCa is now used in JR East's Suica® system, as well as in a number of transport systems around the world. Other applications include the "Edy" electronic money service, the "eLIO" online credit service and various company/organizational ID security systems. At present, 38 million cards using FeliCa chips have been issued worldwide.
DoCoMo launched its mobile internet service i-mode® in 1999, and has gained approximately 40 million subscribers to date. DoCoMo has constantly aimed to upgrade the service by adding various new technologies to enhance interface with other devices, including infrared communications and two-dimensional bar codes. The enhancement of the i-mode handset interface is one primary example of DoCoMo's goal to promote mobile multimedia services by linking i-mode and real businesses.
The Joint Venture will develop the technology for a new IC chip, tentatively named "mobile FeliCa IC", that will integrate mobile phones with the FeliCa technology. The Joint Venture will then implement production and sales licensing agreements with chip manufacturers, and work to create a platform whereby content providers can offer mobile services that feature both flexibility and security. The mobile FeliCa IC and service platform will be developed in an open environment and provided to the widest possible range of mobile telecommunications operators and content providers.
Through this platform, customers will be able to use their mobile phones to enjoy services previously only available with IC cards, such as transport system payments, electronic money and personal ID security. In addition, use of the telecom infrastructure for mobile phones will also enable new capabilities, such as the direct downloading of value (prepaid money) and additional content-based data. Potential applications of the technology could include electronic ticketing and online credit, which would provide convenience and added value for both providers and customers.
DoCoMo plans to launch a test service for mobile phones equipped with the mobile FeliCa IC chip in December of this year. FOMA® and mova® FeliCa equipped phones are scheduled to go on sale in Japan by the end of Fiscal Year 2004.
Through the operations of this new company, Sony and DoCoMo aim to strengthen the market and also create new technological opportunities within the mobile phone sector. At the same time, they will energetically promote the FeliCa technology service platform in order to become a pillar of the rapidly emerging world of contactless IC services. - nttdocomo.com
|
a SMART environment? surveillance grid? command & control?
|
|
Imagine If only you could work in a building where you could keep your office as you like it, icicle-cold, while your neighbor turns hers into a sauna. If only your office lights and computer could flicker on every morning when you swiped your security card in your building's lobby, so that you would be ready to work when you sat down with your first cup of coffee. And while we're on this flight of fancy, wouldn't it be reassuring to know that your building would shield you from harm in the event of an earthquake, or even a chemical or biological attack? Buildings could do all these things and more, if only they had brains.
more
|
|
|
The brainiac of buildings, the U.S. Pentagon, opened for business on 12 September 2001, the day after terrorists crashed a plane into it. Thanks to a network of digital sensors and controllers that let operators close dampers and turn off fans, the fire from the crash was confined to one wedge of the building. -
now imagine a global sytem of SMART autonomous environments...
which can be hacked into...
and controlled
or destroyed
|
|
|
|
|
view promotional video Echelon Technology Overview
See how technology senses, monitors, and controls device networks (requires broadband connection) |
|
The Echelon Corporation
Echelon Corporation (NASDAQ: ELON) is a pioneer and world leader in control networking - networks that connect machines and other electronic devices - for the purpose of sensing, monitoring and controlling the world around us. Echelon's LonWorks® platform for control networking was released in 1990 and has become a worldwide standard in the building, industrial, transportation, and home automation markets. Launched in 2003, Echelon's Networked Energy Services system is an open, extensible, advanced metering infrastructure that can bring benefits to every aspect of a utility's operation, from metering and customer services to distribution operations and value-added business. In 2005 Echelon released the world's first embedded control network infrastructure, the Pyxos platform, extending the benefits of networking inside machines to the sensors and actuators that make them function.
Echelon is based in San Jose, California, with international offices in China, France, Germany, Italy, Hong Kong, Japan, Korea, The Netherlands, and the United Kingdom. Further information regarding Echelon can be found at http://www.echelon.com.
.
SHAREHOLDERS;
ROCKERFELLAR HOLDINGS, BANKE CREDIT SUISSE, BARCLAYS, MELLON , MORGAN STANLEY, JP MORGAN CHASE, USB AG, GOLDMAN SACHS, BANK OF AMERICA, OPPENHEIMER FUNDS, LEHMEN BROS, CITIGROUP, DEUTCHE BANK, BANK OF NEW YORK, WELLS FARGO etc..etc..
|
so in order to gain access to goods and services -
all citizens will have to obey this system:
All citizens will be prone to spying & control
and virus / hacking will provide a culture of
continuous upgrade via FEAR
This fear is to be managed
via a secret backdoor program
to these environmental control systems -
it is the PROMIS system
| WHAT IS PROMIS? Global surveillance access to the cashless society...
Based on their knowledge and belief, the Hamiltons [William and Nancy, owners of Inslaw] have alleged that high level officials in the Department of Justice conspired to steal the Enhanced PROMIS software system. As an element of this theft, these officials, who included former Attorney General Edwin Meese and Deputy Attorney General Lowell Jensen, forced INSLAW into bankruptcy by intentionally creating a sham contract dispute over the terms and conditions of the contract which led to the withholding of payments due INSLAW by the Department.
The Hamiltons maintain that, after driving the company into bankruptcy, Justice officials attempted to force the conversion of INSLAW's bankruptcy status from Chapter 11: Reorganization to Chapter 7: Liquidation. They assert that such a change in bankruptcy status would have resulted in the forced sale of INSLAW'S assets, including Enhanced PROMIS to a rival computer company called Hadron, Inc., which, at the time, was attempting to conduct a hostile buyout of INSLAW. Hadron, Inc., was controlled by the Biotech Capital Corporation, under the control of Dr. Earl Brian, who was president and chairman of the corporation.
The Hamiltons assert that even though the attempt to change the status of INSLAW's bankruptcy was unsuccessful, the Enhanced PROMIS software system was eventually provided to Dr. Brian by individuals from the Department with the knowledge and concurrence of then Attorney General Meese who had previously worked with Dr. Brian in the cabinet of California Governor Ronald Reagan and later at the Reagan White House.
According to the Hamiltons, the ultimate goal of the conspiracy was to position Hadron and the other companies owned or controlled by Dr. Brian to take advantage of the nearly 3 billion dollars, worth of automated data processing upgrade contracts planned to be awarded by the Department of Justice during the 1980's. Information obtained by the Hamiltons through sworn affidavits of several individuals, including Ari Ben- Menashe, a former Israeli Mossad officer, and Michael Riconosciuto, an individual who claims to have ties to the intelligence community, indicated that an element of this ongoing criminal enterprise by Mr. Meese, Dr. Brian and others included the modification of the Enhanced PROMIS software by individuals associated with the world of covert intelligence operations.
The Hamiltons claim the modification of Enhanced PROMIS was an essential element of the enterprise, because the software was subsequently distributed by Dr. Brian to intelligence agencies internationally with a "back door" software routine, so that U.S. intelligence agencies could covertly break into the system when needed. The Hamiltons also presented information indicating that PROMIS had been distributed to several Federal agencies, including the FBI, CIA, and DEA.
- Real History archive
|
QUESTION for the NSA / Daarpa and it's corporate buddies
If it is your own system,
is it still called hacking?
|
|
Power grid vulnerable?
"Our people drove to a remote substation," he recalled.
"Without leaving their vehicle, they noticed a wireless network antenna.
They plugged in their wireless LAN cards, fired up their notebook computers,
and connected to the system within five minutes because it wasn't using passwords.
"Within 10 minutes, they had mapped every piece of equipment in the facility," Blomgren said.
"Within 15 minutes, they mapped every piece of equipment in the operational control network.
Within 20 minutes, they were talking to the business network and had pulled off several business reports.
They never even left the vehicle." -
source
|
|
The Synarchist network: The Octopus
The following is taken from The Octopus: Secret Government and the Death of Danny Casolaro:
One of the ways in which Jimmy Carter may have "bruised the Octopus", as Casolaro says, was through
the imposition of a 1979 embargo on the shipment of arms to Iran. Certainly that bruise healed quickly.
Octopus familiar Ted Shackley appears, after his alleged retirement from the CIA in 1979, in 1984 negotiations
for the shipment of arms to Iran by the Reagan administration. Shackley passed information from Iranians
General Manucher Hashemi and Manucher Ghorbanifar, who had held influential positions in the SAVAK
secret police under the Shah, and now were close to the Ayatollah Khomeini, to Oliver North and alleged
P2 member Michael Ledeen in the White House. The Iranians suggested that arms shipments to "moderates"
such as themselves in Iran could do much to prevent the Ayatollah from taking sides with the Soviets, and
could speed the release of the American hostages. The billions of dollars of arms shipments began, using
Israel, Taiwan, and South Korea as middlemen, as early as 1981, with some of the profits from the Iranian
shipments being diverted to help the contra cause in Nicaragua.?.
The National Endowment for Democracy has been alleged to be a private intelligence network with the purpose
of establishing a fascist, corporatist world state, a theme which also seems to inform the movements of Casolaro's
Octopus. The model of this state can be observed in Michael Ledeen's book, Universal Fascism, in
which he extolls a fascist state based upon the ideals of Gabriele d'Annunzio, Mussolini's predecessor. Ledeen
was connected to P 2, which was in turn connected to the NSC. Reporting directly to North (as well as being a
consultant in the Pentagon and State Department) was Michael Ledeen. Ledeen was responsible for obtaining
Israeli Mossad spy Jonathan Pollard his job in the Department of the Navy, for establishing a line of Israeli influence
into the NSC, and is known in Italy to have been a member of the P2 (Propaganda Due) Masonic lodge. P2, with a
membership believed to include Henry Kissinger and Alexander Haig, is the organization known to have taken over
the highest levels of Italian government and responsible during the 70s and 80s for an attempted bankrupting of the
Vatican, in an alliance that linked the P2, the KGB, and major networks of drug trade.The Wall Street Journal
detailed a meeting between Alexander Haig, Michael Ledeen, and high ranking P 2 member and number two man in
Italian intelligence Francesco Pazienza. Pazienza is said to have been involved in shipments of US arms to Iran arranged
by the Reagan administration.
DOJ had a backdoor added into the program so that the U.S. could access the files of whoever they sold the
PROMIS program to, including the governments of Israel and Canada.
This led to further revelations and
meetings with various informants that further revealed a complex web of deceit leading down some surprising
avenues. Casolaro now changed his plans to writing a novel, perhaps even presenting it as fiction in order
to avoid scaring off publishers. But before this happened, Casolaro was found dead from what was an obviously
staged suicide and many of his notes disappeared. -
file
Much of this material will be familiar to investigators, reformers, and conspiracy buffs. But Thomas and Keith have found some new material and put the pieces together in some new ways that make sense. Time will tell how much of it is true. But the evidence, if not all valid, certainly needs to be explained.
If you thought all you had to worry about was the feds reading your email, or perhaps picking up the RF from your computer keyboard, consider what is said in an interview in this book with Michael Riconosciuto, the computer expert who modified the PROMIS package for the U.S. government:
Q: There was that one interview with [William] Hamilton where he was talking about how PROMIS is some kind of system that includes chips that broadcast directly to NSA satellites.
MR: They are not chips as such. The existing chips in the machine are tricked into doing it. I'm getting ready to go on television explaining that chapter and verse.
Q: On national television?
MR: German television. I will explain in hardcore, unambiguous technical terms how it's done. Unambiguous to people who are technically competent.
Q: When I describe these things to other people they say "That's not possible", particularly people who like to think of themselves as computer jocks. My thought is that ordinary people with PCs can do incredible things now, particularly with the CD ROM stuff.
MR: If you know what you're doing.
Q: But the people who actually invest enormous amounts of money and resources into it, like the National Security Agency, can do things untold, I'm sure.
MR: I'm letting the cat out of the bag where PROMIS is with the NSA. It's in the MOSIS program. The Metal Oxide Semiconductor Implementation System.
more eseential reading
|
Metal Oxide Silicon Implementation Service (MOSIS)
|
Integrated Circuit-Based Fabrication Technologies and Materials
A hallmark of the microelectronics industry is the sustained exponential growth in the performance and complexity of ICs over the past four decades. As complexity and speed have increased, the cost of logic functions, memory, and central processing units (CPUs) has dropped dramatically. The IC field has demonstrated an ability to develop new fabrication processes and materials that are both manufacturable and reliable.
The allure of the emerging field of MEMS is that it can exploit the microelectronics fabrication and materials infrastructure to create low-cost, high-performance systems. The goal is to achieve the levels of performance, manufacturability, reliability, and low costs that are normally associated with microelectronic products. This chapter examines the strengths of various IC-based technologies and their uses for MEMS.
STRENGTHS OF THE INTEGRATED CIRCUIT PROCESS
At least eight characteristics of the IC process have led to its phenomenal growth. Examining these characteristics can provide a helpful perspective for MEMS development. ICs are batch-fabricated so that a great number of circuits and hundreds of millions of electronic devices can be fabricated simultaneously on the surfaces of many wafers. In terms of first-principle effects, it is no more expensive to build 100 circuits on a wafer than it is to build only one. Because interconnection of the enormous numbers of devices is part of the fabrication process, potentially error-prone assembly steps, as well as connection failures during operation, are avoided. These desirable characteristics of batch fabrication are key to the low costs, manufacturability, and reliability associated with ICs.
In current IC production, a common set of materials and repeated process steps can be used to manufacture numerous circuits that may, in turn, be used by many diverse designers. In a typical IC process being used today, materials, basic circuit building blocks, and wiring and design rules are standardized. This standardization has led to a fundamental mastery of technologies and engineering for IC production. New products, designs, and extensions of technology continue to leverage the significant knowledge base that has been developed over the past 40 years.
Using the IC planar processes, the sizes and configurations of microelectronic elements are defined by computer-drawn figures. By exploiting photolithographic techniques, device features can be controlled at the submicrometer level. This control has led to fantastically high performance coupled with very high device density in many products, such as the computer-on-a-chip.
Computer techniques to aid in IC design have evolved to an extremely sophisticated level. The process, circuit function, device operation, and layout can all be simulated and designed with computers. Interaction among diverse groups of designers and users can be conducted through the exchange of software. The maturity of CAD methodologies for integrated circuits has contributed greatly to the success of ICs.
The IC process uses one of the cleanest and most carefully monitored fabrication environments of any large-scale production process. Although this environment is costly to implement, it leads directly to process controls that have increased the yield and reliability of products.
The processes used to produce ICs are very carefully controlled with in-process test structures that are typically made an integral part of the production sequence. The control of patterning and the degree to which impurities can be repeatably introduced and monitored are typically far more precise than for other manufacturing processes.
Standardized IC production processes are accessible to users on a contract basis through IC foundries. This accessibility is very important because maintaining a modern IC production line is very costly (e.g., costs of Intel production facilities are in the billions of dollars). Thus, although large IC producers typically conduct all of the production steps for the ICs they market, smaller industries can design ICs to be produced at foundries that receive only computer layouts to define the products.
This production mode has been validated over the years through the MOSIS program, which was sponsored by the Defense Advanced Research Projects Agency (DARPA) and the National Science Foundation (NSF). The MOSIS program has served both industry and academic institutions.
source - Microelectromechanical Systems: Advanced Materials and Fabrication Methods (1997)
|
making matter programmable
Mems
Saturday, May 20, 2006
Micro-electromechanical systems (MEMS) MOEMS Micro Optical Electronic Machines
Basic Terminology
Picture an incredibly tiny machine so small that it is not visible to the human eye. Imagine machines no bigger than a grain of sand. Imagine hundreds of these machines aligned on a single silicon chip. . Imagine a world where gravity and inertia carry no importance, only atomic forces and surface structures dominate. A silicon chip with hundreds or thousands of microscopic mirrors adjusting in unison, enabling the all optical network and removing the bottlenecks from the global telecommunications infrastructure. Imagine how different the world would be if miniaturized sensors, and computers could be embedded within materials, coated on surfaces, and spread throughout the environment, essentially making matter programmable You are imagining the microdomain, dominated by an incredible technology known as MEMS.
A MEMS device contains micro-circuitry on a tiny silicon chip into which a mechanical device such as a mirror or a sensor has been installeded. Potentially, such chips can be built in large quantities at low cost, making them cost-effective for numerous applications.
It is a technology that integrates complex electromechanical elements and processing circuitry on a chip, using a combination of fabrication techniques that handles the electronics, similar to the way integrated circuits are made, and processes called “micromachining,” . The end result is a unique and self-contained system that not only detects its environment but also has the capability of actively changing it. For this reason MEMS is also sometimes referred to as SMART MATTER.
Among the presently available uses of MEMS or those under study are:
Global position system sensors that can be included with courier parcels for continual tracking
Sensors built into the fabric of an airplane wing so that it can sense and react to air flow
Optical switching devices that can switch light signals over different paths at 20-nanosecond switching speeds
Sensor-driven heating and cooling systems that would improve energy savings
Basic definitions /terminology
Lab on a Chip technology is of interest in many areas. This technology can be utilized to synthesize chemicals efficiently and cost effectively as well as to carry out biological /clinical analyses, to perform combinatorial chemistry, all on a single, miniaturized device.
Micromaching is basically a self explanatory term. Referring to maching and fabrication at the micro & Nano levels.
Plasma Etching A process utilized in micromachining
Microfluidics a multidisciplinary field comprising physics, chemistry, engineering and biotechnology that studies the behavior of fluids at the microscale and mesoscale. Fluids at volumes thousands of times smaller than a single drop . In addition it concerns the design of systems in which such small volumes of fluids will be used.
Fluid behavior at the micro/nano scale differs from the behavior the we normally obeserve in "macrofluids" Factors such as electrokinetics, surface tension, energy dissipation, begin to dominate reactons.
Microfluidics is used in in micro-thermal and micro-propulsion technologies and gene chip technology.
Optical Switches optical switches are an opto-mechanical switch matrix system.
MEMS micro electronic machines
|
|
|
Accomplishments of DARPA's Very Large Scale Integrated Circuit Program |
| |
Other Architecture Projects
The VLSI program supported research on a number of innovative computer
architectures other than RISC. Most of this work centered on designs
for parallel computers. A range of projects supported a variety of
configurations for linking microprocessors and memory, from the
connection machine to the cube machines for general-purpose computing
and the WARP architectures for special-purpose applications, such as
signal processing. Several of these approaches were commercialized
through start-up companies, such as Thinking Machines Corporation, or
established firms, such as Intel Corporation. Although successful
technologically, many of these designs failed to achieve commercial
success.
MOSIS
DARPA also worked to establish ongoing technical and human
infrastructure for VLSI. Of note was establishment of the Metal Oxide
Silicon Implementation Service (MOSIS). Based on the innovative
MultiProject Chip (MPC) service created by Lynn Conway at Xerox PARC
(Conway, 1981), MOSIS provided university researchers with a means of
quickly manufacturing limited numbers of custom or semicustom
microelectronic devices at reasonable cost. New designs could be
implemented in silicon within 4 to 10 weeks (less than the duration of
an academic term). Prior to MOSIS (and the original MPC service),
academic researchers had few economical ways of implementing and testing
new semiconductor designs, few universities could afford their own
fabrication lines, and the proliferation of different commercial systems
of rules for specifying semiconductor circuit designs--most of which
were kept proprietary--made collaboration between universities and
industry difficult. With MOSIS, researchers could submit designs for
fabrication in a standardized format through the ARPANET or,
subsequently, e-mail. Requests from different researchers were pooled
into common lots and run through the fabrication process, after which
completed chips were returned to the researchers. This system obviated
the need for direct access to a fabrication line or for dealing with the
complexity of arranging fabrication time at an industrial facility, by
providing access to a qualified group of fabrication facilities through
a single interface.
MOSIS was widely used by the academic research community and contributed
to many novel systems. Access to MOSIS was originally limited to the
VLSI research community and other Department of Defense contractors who
linked to it through the ARPANET. After the National Science Foundation
(NSF) assumed responsibility for administering MOSIS in 1982, access was
expanded to include NSF-sponsored researchers and affiliated educational
institutions. In 1984, access was expanded to other qualified users as
well. Altogether, MOSIS was used by researchers at more than 360
institutions by 1989. The number of projects run through MOSIS
increased from 258 in 1981 to 1,880 in 1989. RISC-based designs, such
as RISC I, RISC II, and MIPS, and the geometry engine later
commercialized by SGI were all run through MOSIS during their early
design and testing phases. Prominent VLSI researcher Charles Seitz
commented that MOSIS represented the first period since the pioneering
work of Eckert and Mauchley on the ENIAC in the late 1940s that
universities and small companies had access to state-of-the-art
digital technology.5
Design Tools
DARPA also supported development of tools for designing VLSI devices.
In 1978 and 1979, DARPA funded development of a program for step-level
improvement in the layout of microelectronic devices. The result was
Caesar, an interactive VLSI layout editor that was written in C,
enabling it to run on VAX computers using the Berkeley version of Unix
developed by Bill Joy. Caesar produced CalTech intermediate form files
for use with the MOSIS system and was used to develop the RISC I, RISC
II, and MIPS designs. Further modification made the tool suitable for
more widespread use. A later, more advanced design technology created
at UC-Berkeley, Magic, became even more widely used and formed the basis
for several computer-assisted design systems, including those by VLSI
Technology, Cadence, Valid Logic, Daisy, Mentor Graphics, and Viewlogic.
source - .nap.edu
|
Project superman? Converging Technologies for Improving Human Performance
|
"Examples of payoffs may include improving work efficiency and learning, enhancing individual
sensory and cognitive capabilities, revolutionary changes in healthcare, improving both individual and
group creativity, highly effective communication techniques including brain-to-brain interaction,
perfecting human-machine interfaces including neuromorphic engineering, sustainable and
"intelligent" environments including neuro-ergonomics, enhancing human capabilities for defense
purposes, reaching sustainable development using NBIC tools, and ameliorating the physical and cognitive decline that is common to the aging mind."
MUST READ: Converging Technologies for Improving Human Performance
further excerpts below
|
|
Vision for Enhancing Human Abilities and Societal Performance
Despite moments of insight and even genius, the human mind often seems to fall far below its full
potential. The level of human thought varies greatly in awareness, efficiency, creativity, and accuracy.
Our physical and sensory capabilities are limited and susceptible to rapid deterioration in accidents or
disease and gradual degradation through aging (Stern and Carstensen 2000). All too often we
communicate poorly with each other, and groups fail to achieve their desired goals. Our tools are
difficult to handle, rather than being natural extensions of our capabilities. In the coming decades,
however, converging technologies promise to increase significantly our level of understanding,
transform human sensory and physical capabilities, and improve interactions between mind and tool,
individual and team. This report addresses key issues concerning how to reach these goals.
Each scientific and engineering field has much to contribute to enhancing human abilities, to solving
the pressing problems faced by our society in the twenty-first century, and to expanding human
knowledge about our species and the world we inhabit; but combined, their potential contribution is
vast. Following are twenty ways the workshop determined that convergent technologies could benefit
humanity in a timeframe of 10 to 20 years. Each of these scenarios are presented in detail in the body
of the report:
Fast, broadband interfaces directly between the human brain and machines will transform work in
factories, control automobiles, ensure military superiority, and enable new sports, art forms and
modes of interaction between people.
Comfortable, wearable sensors and computers will enhance every persons awareness of his or her
health condition, environment, chemical pollutants, potential hazards, and information of interest
about local businesses, natural resources, and the like.
Robots and software agents will be far more useful for human beings, because they will operate on
principles compatible with human goals, awareness, and personality.
People from all backgrounds and of all ranges of ability will learn valuable new knowledge and
skills more reliably and quickly, whether in school, on the job, or at home.
Individuals and teams will be able to communicate and cooperate profitably across traditional
barriers of culture, language, distance, and professional specialization, thus greatly increasing the
effectiveness of groups, organizations, and multinational partnerships.
The human body will be more durable, healthy, energetic, easier to repair, and resistant to many
kinds of stress, biological threats, and aging processes.
Machines and structures of all kinds, from homes to aircraft, will be constructed of materials that
have exactly the desired properties, including the ability to adapt to changing situations, high
energy efficiency, and environmental friendliness.
A combination of technologies and treatments will compensate for many physical and mental
disabilities and will eradicate altogether some handicaps that have plagued the lives of millions of
people.
National security will be greatly strengthened by lightweight, information-rich war fighting
systems, capable uninhabited combat vehicles, adaptable smart materials, invulnerable data
networks, superior intelligence-gathering systems, and effective measures against biological,
chemical, radiological, and nuclear attacks.
Anywhere in the world, an individual will have instantaneous access to needed information,
whether practical or scientific in nature, in a form tailored for most effective use by the particular
individual.
Engineers, artists, architects, and designers will experience tremendously expanded creative
abilities, both with a variety of new tools and through improved understanding of the wellsprings
of human creativity.
The ability to control the genetics of humans, animals, and agricultural plants will greatly benefit
human welfare; widespread consensus about ethical, legal, and moral issues will be built in the
process.
The vast promise of outer space will finally be realized by means of efficient launch vehicles,
robotic construction of extraterrestrial bases, and profitable exploitation of the resources of the
Moon, Mars, or near-Earth approaching asteroids.
New organizational structures and management principles based on fast, reliable communication
of needed information will vastly increase the effectiveness of administrators in business,
education, and government.
Average persons, as well as policymakers, will have a vastly improved awareness of the cognitive,
social, and biological forces operating their lives, enabling far better adjustment, creativity, and
daily decision making.
Factories of tomorrow will be organized around converging technologies and increased human-
machine capabilities as "intelligent environment" that achieve the maximum benefits of both
mass production and custom design.
Agriculture and the food industry will greatly increase yields and reduce spoilage through
networks of cheap, smart sensors that constantly monitor the condition and needs of plants,
animals, and farm products.
Transportation will be safe, cheap, and fast, due to ubiquitous realtime information systems,
extremely high-efficiency vehicle designs, and the use of synthetic materials and machines
fabricated from the nanoscale for optimum performance.
The work of scientists will be revolutionized by importing approaches pioneered in other sciences,
for example, genetic research employing principles from natural language processing and cultural
research employing principles from genetics.
Formal education will be transformed by a unified but diverse curriculum based on a
comprehensive, hierarchical intellectual paradigm for understanding the architecture of the
physical world from the nanoscale through the cosmic scale.
If we make the correct decisions and investments today, any of these visions could be achieved within
twenty years time. Moving forward simultaneously along many of these paths could achieve a golden
age that would be a turning point for human productivity and quality of life. Technological
convergence could become the framework for human convergence (Ostrum et al. 2002).
The twenty- first century could end in world peace, universal prosperity, and evolution to a higher level of
compassion and accomplishment. It is hard to find the right metaphor to see a century into the future,
but it may be that humanity would become like a single, distributed and interconnected brain based
in new core pathways of society. This will be an enhancement to the productivity and independence
of individuals, giving them greater opportunities to achieve personal goals.
|
read that again:
"humanity would become like a single, distributed and interconnected brain..."
will you be told?
|
|
Could a system of Optical sattelite tracking, 3d radar, RFID, Bluetooth & Brain-interface technology
come to resemble a form bio-tech remote viewing? Will this spy network be able to hack into your brain via a secret backdoor and sense what you sense?
|
|
|
Is it just my imagination?
example:
normal surviellance: find target = spy & view target
new concept: find target = locate window, spy and view through target
Any human will be the 'window'
|
|
and will be located via the DNA database - used as you would a telephone directory
The upgradable nano-scale RFID / MMEA chip will be your passport to goods and services
|
|
|
|
The system admin can hack into anyones braincode
- via electrical signal to and from the brain.
The brains signal is then decoded and remotely watched as a hologram
|
|
3D Radar
CEA-FAR (3D) Radar is a fixed, active phased-array radar incorporating the latest technologies to provide unrivalled performance, at a price that is competitive with modern 2D radars.
CEA -FAR is available in a number of configurations to meet operational, physical and budgetary requirements. It provides both multi-function and multi-role capabilities, and is capable of tracking air and surface targets, both moving and stationary, in maritime and land environments.
CEA-FAR applications include self-defence, short and medium range surveillance, and fire control systems.
smaller 3D phased Array
|
3D TV!!!!
A display that is so real you can almost touch the objects as they come out of the screen in 3D has been a dream for many years.
But no longer, Philips technology is now ready to do just that by bringing together the Company's strengths in LCD manufacture, optical screen design and image processing software and hardware. The displays can be used without wearing special glasses and represent a new way of looking at things in medical applications, 3D gaming and even 3D TV. -
Philips 3-D Display Uses Patented Lens Technology And New Software
philips.com
|
|
|
the death of privacy - potentially using anyone as a spy
With the possibility of 'secret backdoor technology' being written into this Brain Machine Interface
Memory and perception could also be altered, with the possibility that
ultra secrets could be stored in an unsuspecting citizen.
|
|


 Down with Murder inc.
Down with Murder inc.